21.1 Version Highlights
Cybereason version 21.1 introduces new features, including improved fileless malware protection, new user roles to support federated management of the platform, improvements in Endpoint Controls and support for Linux operating systems with Endpoint Protection features, and many more.
In this topic:
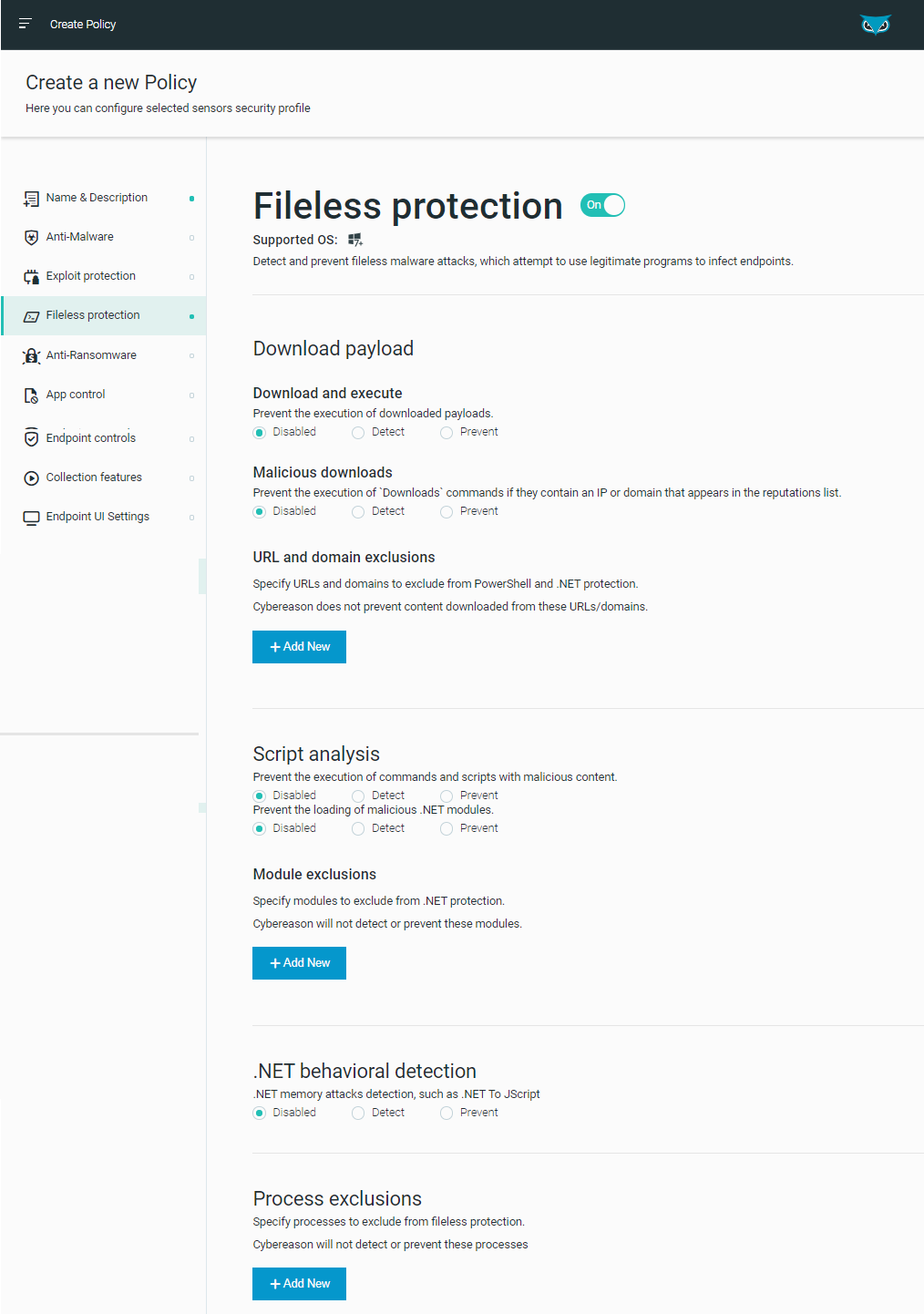
Improved fileless protection
In addition to the Cybereason platform’s existing PowerShell and .NET protection modules, the platform now integrates with Microsoft Anti-Malware Scan Interface (AMSI) to complete its Fileless protection suite. The Fileless protection suite now includes protection against attacks that exploit JScript, VBScript, Office macros, and Windows Management Instrumentation (WMI).
Integrating Cybereason with AMSI provides visibility, collection, detection, and prevention for various engines and products in their modern versions, which include built-in support for AMSI.
New user roles
With version 21.1, user admins assign the new ‘Local analyst L1’ or ‘Local analyst L2’ role to analysts that will interact with sensors in specific sensor groups. When a Local analyst L1 or L2 user is assigned a sensor group, they can only interact with Malops and data pertaining to sensors in that group. This allows system administrators to delegate investigation and Malop management tasks to different users or teams, while limiting the access each team has to other data.
Similarly, user administrators can now assign the ‘Sensor viewer’ role to users who need read access to certain sensor groups.
With both new roles, the user administrator needs to give each user explicit permission to one or more groups using the Permissions section of the Create User screen.
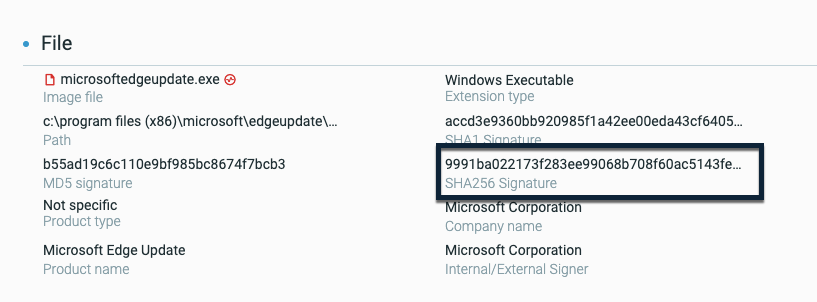
SHA-256 support
We have now added support for SHA-256 file hash values.
Sensors can collect SHA-256 file hash values from files and these details are reported in file details in the Cybereason platform:
In addition, you can add a custom reputation for a SHA-256 file hash value to your organization’s allowlist or blocklist.
IR tool management from the platform
To assist you with incident response, we have added the ability to manage incident response tools with the Cybereason platform. You no longer need to physically install multiple different tools on the machines involved in an incident response process.
Now, you can upload and deploy incident response tools to any machine with a Cybereason sensor installed. After the tool deployment completes, you can run the tool using the tool’s native functionality and commands, and collect the results after the tool finishes running.
You must have the Responder L2 role assigned to manage incident response tool deployment and execution.
Expansion of prevention and response capabilities to Linux sensors
To expand protection provided by our Anti-Malware Signatures mode scans, scheduled and on demand Signature-based scans are now generally available on machines running Linux sensors. When working with a Linux sensor that is assigned a policy with Anti-Malware > Signatures mode enabled, scheduled and on demand scans run automatically according to policy settings. On access scans are not currently supported.
In addition, to provide response capabilities across additional operating systems, you can now isolate Linux machines using the machine isolation feature.
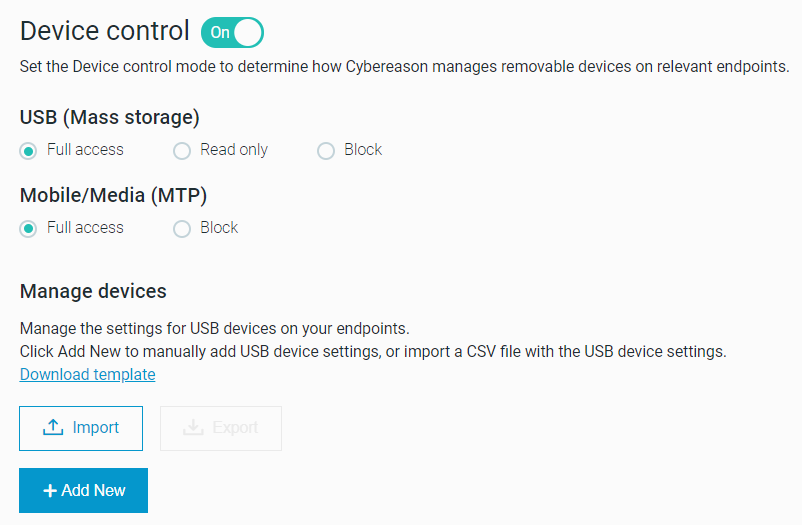
Device control enhancements
To better protect against potentially malicious USB devices, the Device control feature now supports Media Transfer Protocol (MTP) devices, including mobile devices, and additional types of USB devices, such as USB keyboards.
We have also added the following capabilities to enhance the device management experience:
Set the Device control feature to one of three modes: Full access, Read only, or Block. Learn more
Upload a list of USB devices using a CSV file. Learn more
To allow protection for USB devices on additional operating systems, the Device control feature is now supported on endpoints running Linux operating systems.
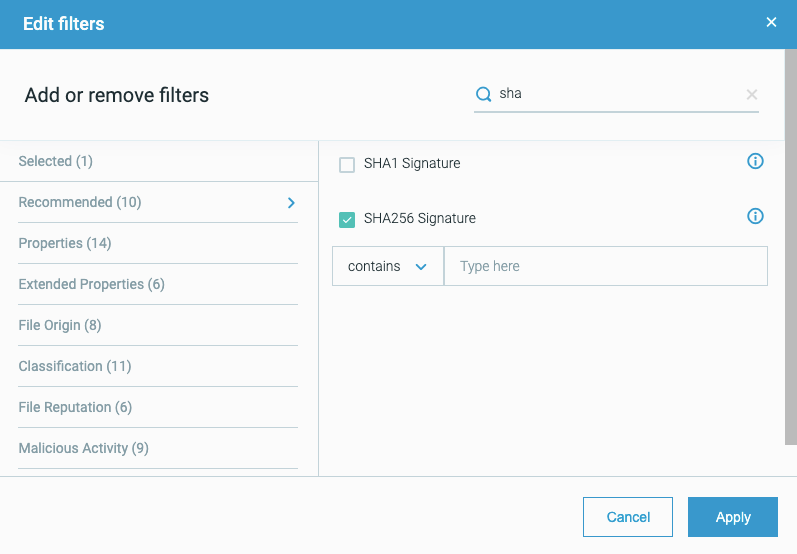
Improve investigations with the ability to create filters from results
Analysts can narrow down the results of an on-going query by selecting individual values from the results to add to the query filter. For example, you may want to filter by a specific command line value you see in the Command line column of the query results. To do this, use Alt/Cmd and click on the value in the query’s results grid. The value is added as a filter to the filter box. Learn more.
Update Responder L1 and Responder L2 role permissions
We have updated the name of the Responder role to Responder L1 in addition to adding the Responder L2 role used for incident tool management tasks.
The Responder L1 role has also been updated to include access to the File search screen as part of its permissions
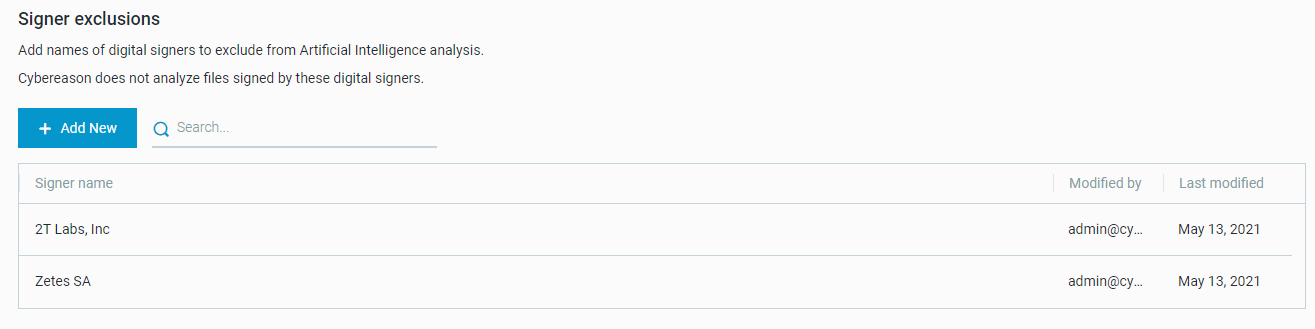
Add exclusions based on the digital signer
To help reduce false positive results and prevent trusted files from triggering Malops, we have added the ability to exclude digital signers from Artificial Intelligence analysis scans. Learn more
Improve sensor group assignment logic
To improve sensor group assignment, with 21.1, when you manually assign a sensor to a group, group assignment logic does not apply to that sensor. The manually-assigned sensor becomes a static member of the group, and does not move between groups.
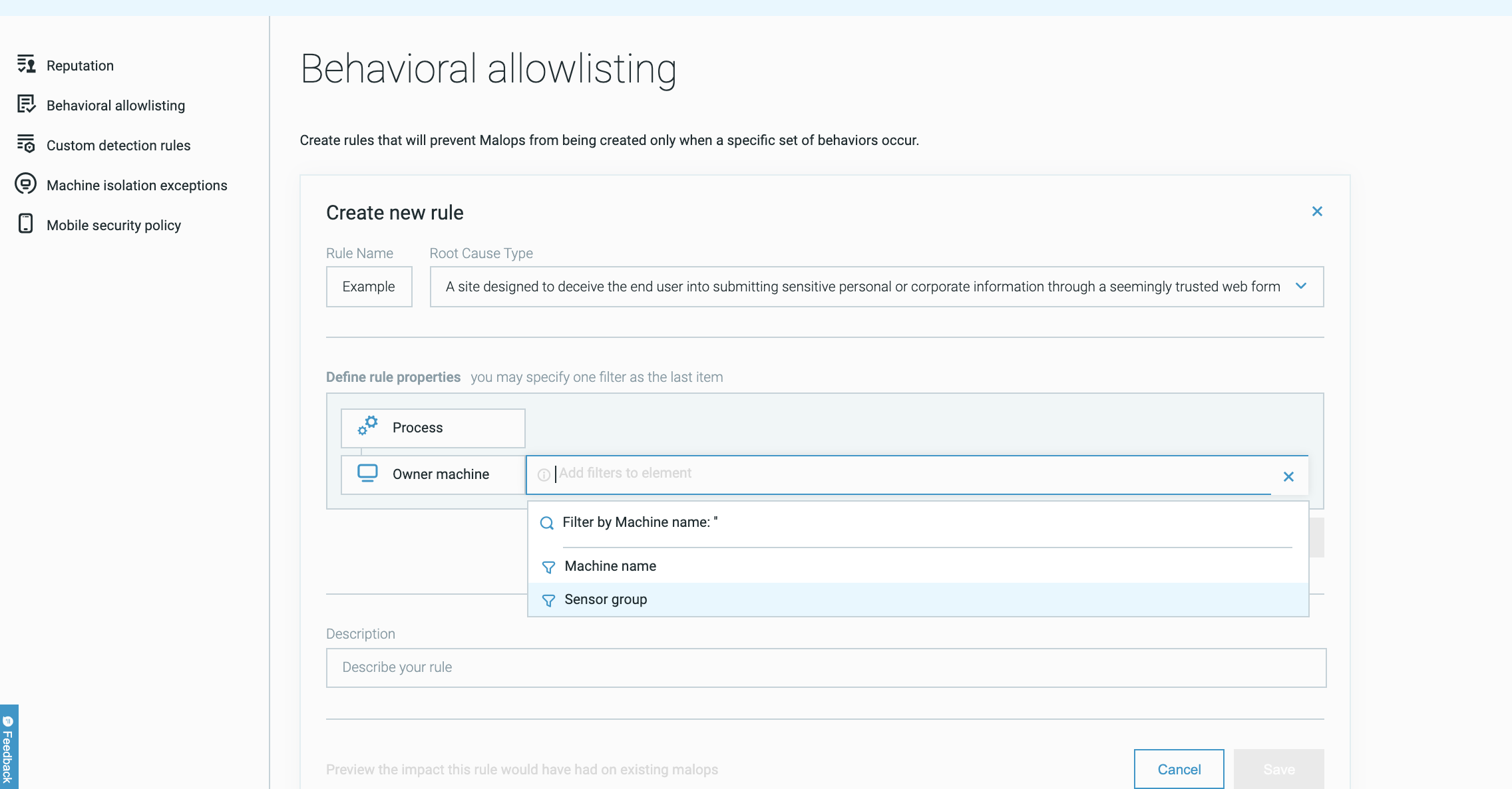
Use behavioral allowlisting rules with sensor groups
Users with the ability to create behavioral allowlisting rules can now apply a specific rule to a specific group of sensors, ensuring that the rule only prevents Malop generation for behaviors on a specific group of machines. To apply the behavioral allowlisting rule to only sensors in a specific group, use the Owner machine Element with the Sensor group filter and the group ID.
Default password policy strengthening
Beginning with version 21.1.143, new environments will have the following default password policy settings:
Two Factor Authentication (TFA) is enabled
Password complexity is ‘Strict’
User lockout policy is enabled
Administrators can configure these settings in the Settings screen, although Cybereason recommends keeping the new defaults settings.
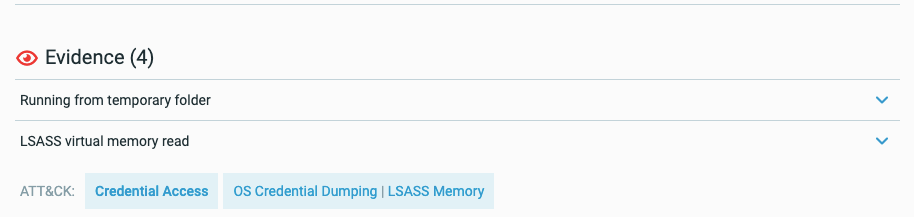
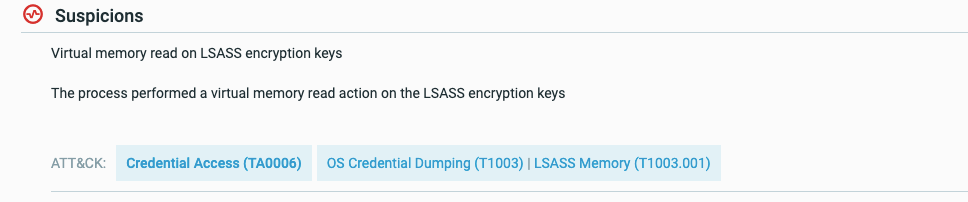
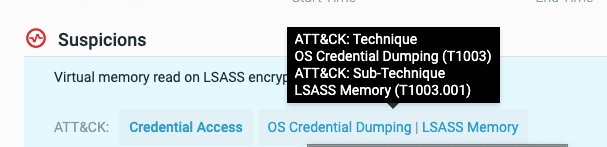
MITRE tags in the Malop Details
For those suspicions and evidence that map to a specific MITRE ATT&CK tactic, technique, or sub-technique, we have added tags with the suspicion and evidence name indicating the name and number for the tactic, technique, or sub-technique:
You can click on any of these tags to open the relevant page in the MITRE ATT&CK matrix site.
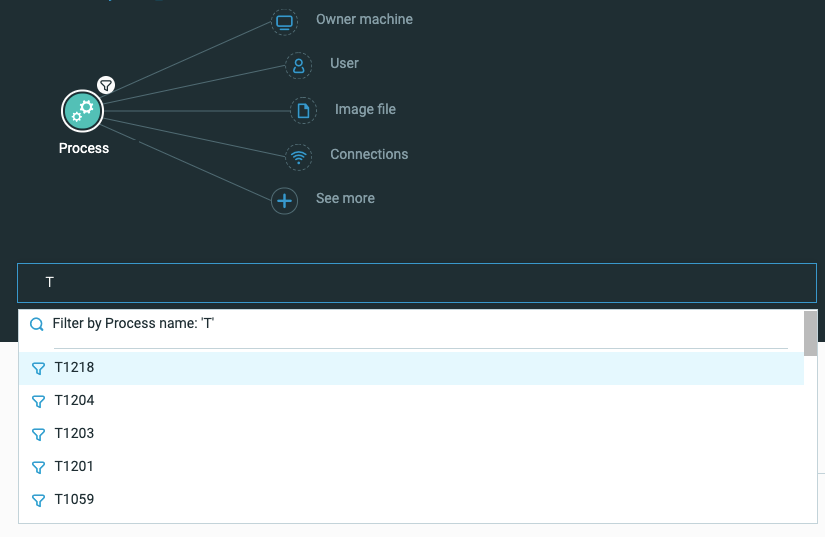
Furthermore, you can use these tags to search in the Investigation screen:
New OS support
We now support deployment of sensors on machines running the following operating systems:
Windows 10 21H1
SLES 15