21.1 All Features
The tables in the following sections list all the features included in all minor releases included in version 21.1 LTS, organized by minor versions. All the features listed below are also included in the 21.1 LTS version.
The tables contain the following information about each feature:
The feature area
A description of the changes
Whether you need to update your server or sensor to the version listed
The supported operating system for the machines for the sensor
The sensor and server versions required to utilize the feature
The tables contain the following information about each feature:
The feature area
A description of the changes
Whether you need to update your server or sensor to the version listed
The supported operating system for the machines for the sensor
The sensor and server versions required to utilize the feature
Version 21.1.542 (Service Pack)
Issue |
Area |
Description |
Required Update |
Sensor OS |
|---|---|---|---|---|
DFND-13560 |
Sensor installation |
When installing or upgrading a sensor on Linux machines, the installation log had unexpected results, including numerous repeated and redundant lines in the log. This was due to the results of a verification of the presence of prerequisite libraries on the machine. We have resolved this issue and the log entries have been streamlined for better use. |
Sensor and server |
Linux |
DFND-14202 |
Sensor performance |
Frequently, the sensor was not able to connect to the Dynamic Sensor Connections service to get sensor content updates. This occurred when the token was expired and a new token was not downloaded. This issue has been resolved and the sensor is now able to continually connect to the Dynamic Sensor Connections service as expected on a continuous basis. |
Sensor and server |
Windows |
Version 21.1.524 (Service Pack)
Issue |
Area |
Description |
Required Update |
Supported OS |
|---|---|---|---|---|
DFND-23332 |
Sensor installation/sensor upgrade |
We have added a prerequisite check to the sensor installation and sensor upgrade processes to ensure that you have the Sectigo certificate required by the Microsoft Virus Initiative (MVI) installed on the machine. |
Sensor and server |
Windows |
DFND-23654 |
Sensor performance |
In certain cases, when using the .NET part of Fileless protection, some programs such as the Windows Event Viewer and PowerShell, for example, were unable to run on the machine. We have resolved this error and programs on the machine should work as expected with Fileless Protection enabled. |
Sensor and server |
Windows |
DFND-28973 |
User management |
When trying to add new users with an .inc domain in the email address, the Cybereason platform failed to add these users correctly. This issue has been resolved and you can add users with a .inc domain in the user email address. |
Server |
N/A |
Version 21.1.500 (Service Pack)
Issue |
Area |
Description |
Required Update |
Supported OS |
|---|---|---|---|---|
DFND-17947 |
Predictive Anti-Ransomware |
For users in Japanese environments, we have updated the title of the Predictive Ransomware Protection screen to 予測型ランサムウェア保護. |
Server |
N/A |
DFND-28883 |
Anti-Malware scans |
We have updated the logs recorded when you perform an Anti-Malware scan to also report the Static Analysis prediction score for a file and the PE file type for each file. |
Sensor and Server |
All |
DFND-13846 |
Sensors screen |
At times when an environment uses a proxy, the Internal IP address field value displayed for a sensor in the Sensors screen was 127.0.0.1 instead of the real IP address of the sensor due to the looping of the address as part of the proxy. We have updated the configuration of the sensor to report the correct IP address for the machine in the Sensors screen. |
Sensor and server |
All |
DFND-19860 |
Sensor installation |
When uninstalling a sensor from the latest version, the uninstallation failed with an error that the sensor installation folder was still in use. We have resolved this issue and the uninstallation works as expected. |
Sensor and server |
Windows |
DFND-20802 |
Behavioral Document Protection |
Previously, detection rules used with Behavioral Document Protection did not create detections when the document files contained Japanese characters. We have resolved the issues and detection rules work even when the document file contains Japanese characters in the name. |
Sensor and server |
Windows |
DFND-20656 |
Sensor installation |
When uninstalling the sensor after upgrading to the latest 21.1 version, the uninstall operation failed, unless you restarted the machine. We have resolved the issue and the uninstall operation works as expected without a restart of the machine. |
Sensor and server |
Windows |
DFND-21496 |
L3 analyst role |
Previously, users with the L3 analyst role were not able to view and edit machine isolation exception rules. We have resolved this issue and users with the L3 analyst role are able to view and edit as expected. |
Server |
N/A |
DFND-22698 |
Linux sensors |
When trying to install sensors on Linux machines running Oracle Linux operating systems, the installation would fail as the minionhost process did not work properly. This issue has been resolved and installations on Oracle Linux machines work properly. |
Sensor and Server |
Oracle Linux |
DFND-22993 |
Sensors screen |
When exporting details on sensors to a CSV file with the API, the list of sensors was incomplete. For example, the exported might contain 10,000 lines instead of the expected 40,000 lines. This issue has been resolved and the CSV file exports with the correct amount of data. |
Server |
N/A |
DFND-23407 |
Detection rules |
Due to a change in the sensor certificate name, Attempt to manipulate Cybereason sensor false-positive detections were generated for the sensor’s amsvc.exe and activeconsole.exe processes. This issue has been resolved and these detections should no longer be created for the sensor processes. |
Server |
N/A |
DFND-28702 |
Remediation |
When viewing the Response History screen, if you clicked the Back button in your browser, you were returned to the default Discovery Board page, instead of the previous screen. This issue has been resolved and clicking the Back button returns you to your previous screen. |
Server |
N/A |
Version 21.1.482 (Service Pack)
Issue |
Area |
Description |
Required Update |
Supported OS |
|---|---|---|---|---|
DFND-19717 |
Device Control |
When using Device Control, after you disable or enable a Read Only for USB devices, endpoint machine users no longer need to re-mount a USB device to ensure that the sensor enforces the Read Only policy setting. |
Sensor and server |
Windows, Linux |
DFND-20395 |
Sensor installation |
As part of the initiative to meet MVI (Microsoft virus initiative) requirements, we have added a warning and a logic to stop installation when you try to install a sensor on a machine running Windows 7. This installation prevention is due to the fact that the Sectigo certificate used for the MVI compliance is not supported on Windows 7. |
Sensor and server |
Windows |
DFND-22221 |
Anti-Ransomware |
In previous versions, the crsdll.dll file required for Anti-Ransomwaredid not upgrade properly as part of the version upgrade flow. We have resolved this issue and this DLL file will upgrade correctly in the overall upgrade flow. |
Sensor and server |
Windows |
DFND-15669 |
Process information collection |
At times, when the sensor collected details on the command lines used by processes, the collector on the sensor would add an extra space in the command line string that was sent to the detection server. As a result, if you built a behavioral allowlisting rule to exclude the command line from creating a Malop, the behavioral allowlisting rule would not correctly trigger Malops. This issue has been resolved and the command line is collected and sent to the Detection server correctly without the extra spaces. |
Sensor and server |
Windows |
DFND-681 |
Machine isolation |
By default, actions sent to offline sensors are queued for 3 days. If, after 3 days, the sensor has not come back online, the action is no longer queued and will not execute if the sensor comes back online at a later time. Now, the queued period can be customized. |
Sensor and server |
All |
Version 21.1.463 (Service Pack)
Issue |
Area |
Description |
Required Update |
Supported OS |
|---|---|---|---|---|
N/A |
Sensor certificates |
Sensor binaries are now signed by Sectigo cross certificate to meet MVI (Microsoft’s virus initiative) requirements. Learn more |
Sensor and server |
Windows |
DFND-17002 |
Sensor upgrade |
If you upgrade a sensor that has had proxy settings changed, after the upgrade, the proxy settings are retained. If the sensor upgrade package contains new proxy settings, the updated proxy settings override the sensor’s existing proxy settings. |
Sensor and server |
All |
DFND-16940 |
Anti-Malware scans |
We have updated the configuration used by the Cybereason platform’s Anti-Malware scans to better handle scans of large archives (e.g. .zip files), including:
The option to increase the file size allowed for a scan is not enabled by default. Open a Technical Support case to enable this option. |
Sensor and server |
Windows |
DFND-10830 |
Platform license agreement |
We have updated the End User License Agreement (EULA) for the Cybereason platform. The first user to sign in to the Cybereason console after you deploy this version will be required to accept the new agreement, even if you accepted previous versions of the agreement. |
Server |
N/A |
DFND-5100 |
Sensors screen |
We have updated the configuration the Cybereason platform uses to display information about sensors on machines with unsupported OS versions. Now, the Sensors screen will display Other for these sensors to enable you to better filter these machines. |
Server |
N/A |
DFND-17884 |
Anti-Malware scans |
On-demand scans now scan files that contain any Unicode characters in the file name. |
Sensor and server |
Windows |
DFND-18658 |
Behavioral allowlisting |
When previewing the effect of a behavioral allowlisting rule in Japanese, the preview would display an error for invalid query syntax. This issue has been resolved and the preview of the rules in Japanese displays the rules correctly. |
Server |
N/A |
DFND-19310 |
Malop remediation |
When you have a sensor policy with the option to Quarantine malicious files selected (in the Anti-Malware section of the sensor policy edit screen), if you have a MalOp with a quarantined file that you mark to Exclude, it was not possible to remove the quarantined file from the quarantine file location. This issue has been resolved and you are now able to remove the file from quarantine. |
Server |
N/A |
DFND-15804 |
Anti-Malware |
In rare cases, the Anti-Malware service had recurring crashes and was not able to recover. This issue has been resolved as we improved our Windows AV service to recover in a more robust way in during these rare cases. |
Sensor and server |
Windows |
DFND-22221 |
Anti-Ransomware |
In previous versions, the crsdll.dll file required for Anti-Ransomware did not upgrade properly as part of the version upgrade flow. We have resolved this issue and this DLL file will upgrade correctly in the overall upgrade flow. |
Sensor and server |
Windows |
Version 21.1.442 (Service Pack)
Issue |
Area |
Description |
Required Update |
Supported OS |
|---|---|---|---|---|
DFND-15182 |
Data collection (Windows) |
We have updated the detection rule logic for APC injections to minimize false-positive rate. |
Sensor and Server |
Windows |
DFND-16940 |
Windows AV |
We made configuration improvements to the archive scan to prevent it from timing out. |
Sensor and Server |
Windows |
DFND-13342 |
User Management |
Users with notifications enabled did not receive notifications that a Malop with an unknown detection type was created. This issue has been resolved. |
Server |
N/A |
Version 21.1.421 (Service Pack)
Issue |
Area |
Description |
Required Update |
Supported OS |
|---|---|---|---|---|
DFND-13558 |
Linux AV |
If a malicious process is detected by an Anti-malware quick scan, only the malicious process is killed. Other members of the process group continue to run as normal. |
Sensor and Server |
Linux |
DFND-14925 |
NGAV |
If an error prevents Anti-Malware from being enabled on an endpoint (for example Other AV Found), we have improved reporting of the error and Anti-Malware automatically becomes enabled on the endpoint once the error is resolved. |
Sensor and Server |
Windows |
DFND-12068 |
Windows AV |
Windows machines with Signature-based analysis enabled, can now receive signature database updates from a Local Update Server (LUS) through a proxy. |
Sensor and Server |
Windows |
DFND-7238 |
MalOp Management |
If an affected machine in a MalOp had an undefined attribute, you could not respond to the MalOp. This issue has been resolved. |
Server |
N/A |
Version 21.1.401 (Service Pack)
Issue |
Area |
Description |
Required Update |
Supported OS |
|---|---|---|---|---|
CYBR-47900 |
Virtualization |
If you created a virtual machine using a golden image with a sensor installed, the sensor on the virtual machine was unable to retrieve the configuration of the applied policy. This issue has been resolved. |
Sensor and Server |
Windows |
Version 21.1.383 (Service Pack)
Issue |
Area |
Description |
Required Update |
Supported OS |
|---|---|---|---|---|
DFND-2826 |
Linux AV |
To improve performance, the Cybereason platform now excludes known and safe processes by default on Linux machines. You can also exclude additional files from Anti-Malware scans based on the name of the process that opens the files. To use this capability, contact Technical Support. |
Sensor and Server |
Linux |
CYBR-51279 |
Custom detection rules |
In the Security profile > Custom detection rules screen, if you created a new custom detection rule with the Process root element and Owner machine element, and tried to add a filter to the Owner machine element, no filter was available and the page became unresponsive. This issue has been resolved, filters are now available and the page is responsive. |
Server |
N/A |
DFND-5607 |
Fileless Protection |
On machines running Windows 10 32-bit with Fileless protection enabled, an error was caused by the DLL used to implement Microsoft Anti-Malware Scan Interface (AMSI). This issue has been resolved. |
Sensor and Server |
Windows |
CYBR-48815 |
Investigation |
On the MalOp details page, if you clicked Menu > Investigate primary root cause, the Investigation screen loaded without the predefined query relevant to the Malop. This issue has been resolved. |
Server |
N/A |
CYBR-52601 |
Sensor Management |
In the Archived sensors report, the number of sensors to be archived was incorrect. This issue has been resolved. |
Server |
N/A |
Version 21.1.361 (Service Pack)
Issue |
Area |
Description |
Required Update |
Supported OS |
|---|---|---|---|---|
CYBR-50613 |
Linux AV |
To improve performance of Anti-malware on access scans on Linux machines, the Cybereason platform now excludes network shares by default. In addition, the Cybereason platform excludes the following mount points on local paths by default:
To exclude additional mount points, contact Technical Support. |
Sensor |
Linux |
CYBR-49468 |
Mac AV |
For sensors on machines running macOS with Anti-malware enabled, on the System > Sensors screen, we have improved the reliability of the status displayed in Sensor status column. |
Sensor |
macOS |
CYBR-49322 |
Mac AV |
macOS developer workloads (such as Git and other developer tools) no longer have performance impacts in combination with Anti-malware on access scans. |
Sensor |
macOS |
CYBR-50381 |
Mac AV |
Anti-malware on access scans no longer have a performance impact on upgrading macOS machines to a newer OS version. |
Sensor |
macOS |
CYBR-50550 |
NGAV |
We have made performance improvements to Signature-based analysis on sensors running on Linux and macOS machines. |
Sensor |
Linux and macOS |
CYBR-50570 |
Sensor Management |
We have improved the startup process of the program that runs the Cybereason icon that appears on the end user’s System Tray. |
Sensor |
Windows |
CYBR-51421 |
Behavioral Prevention |
Fileless protection (AMSI detections) triggered false positive alerts due to scanning process memory in addition to the attack payload. This issue has been resolved, and false positive alerts are no longer triggered. |
Sensor |
Windows |
CYBR-51279 |
Custom detection rules |
In the Security profile > Custom detection rules screen, if you created a new custom detection rule with the Process root element and Owner machine element, and tried to add a filter to the Owner machine element, no filter was available and the page became unresponsive. This issue has been resolved, filters are now available and the page is responsive. |
Server |
N/A |
CYBR-52025 |
NGAV |
If the Anti-Malware > Signatures mode had Ignore network paths and Scan archives enabled, network drives were erroneously scanned. In addition, if Anti-Malware > Signatures mode scanned a large file, the scan was aborted. This issue has been resolved. If Ignore network paths is enabled, network paths are not scanned. |
Sensor |
Windows |
CYBR-51701 |
NGAV |
If Anti-Malware > Signatures mode was set to Disinfect, in the Investigation screen and Malware alerts screen, Detection Events data collected from macOS or Linux machines was missing information. This issue has been resolved. |
Sensor |
Linux and macOS |
CYBR-51449 |
NGAV |
On machines running Linux CentOS 6, if Anti-Malware > Signatures mode was enabled and then disabled, the Cybereason platform successfully aborted the Signatures mode update on the sensors but an error message was sent to the CrAv.log. This issue has been resolved. |
Sensor |
Linux |
CYBR-51397 |
NGAV |
On machines running Linux CentOS 6, if the Anti-Malware > Signatures mode was enabled, on the System > Sensors screen, the Signatures mode status remained in Initializing status and Signatures mode was not successfully enabled on the sensor. This issue has been resolved, Signatures mode is successfully enabled and the correct status is displayed on the System > Sensors screen. |
Sensor |
Linux |
CYBR-39647 |
NGAV |
Following a signature database update, sensors on versions 20.2.182 and 20.1.386, contained two duplicate lines in the Anti-Malware signatures log (AmSvc.log on Windows machines and CrAv.log on macOS and Linux machines). This issue has been resolved. |
Sensor |
All |
CYBR-51939 |
User Management |
In versions 21.1 and above, on the Settings screen, in the Password policy section, if the WebApp server was restarted, the Complexity option reverted to the default value (Strict). This issue has been resolved. |
Server |
N/A |
Version 21.1.342 (Service Pack)
Issue |
Area |
Description |
Required Update |
Supported OS |
|---|---|---|---|---|
CYBR-50472 |
Linux AV |
On Linux machines, the Cybereason platform now supports the option to perform on file access scans by default. You no longer need to contact Technical Support to enable this option. |
Sensor |
Linux |
CYBR-50550 |
NGAV |
We have made performance improvements to Signature-based analysis on Linux and macOS machines. |
Sensor |
Linux and macOS |
CYBR-47281 |
OS Support |
We now support sensors running on Windows 10 21H2 machines. |
Server |
Windows |
CYBR-51279 |
Custom detection rules |
In the Security profile > Custom detection rules screen, if you created a new custom detection rule with the Process root element and Owner machine element, and tried to add a filter to the Owner machine element, no filter was available and the page became unresponsive. This issue has been resolved, filters are now available and the page is responsive |
Server |
N/A |
CYBR-50179 |
Sensor Management |
On the System > Sensors screen, if you sorted the sensors using the Last seen column, the online sensors were not displayed in the correct order. This issue has been resolved. |
Server |
N/A |
CYBR-27970 |
Sensor Management |
If you added a new site, on the System > Sensors screen, the site was not visible until the screen was refreshed. This issue has been resolved. |
Server |
N/A |
CYBR-47920 |
User Management |
If you created a new user with the Change password on next login check box selected, or if a user’s password expired, after the password was changed the user was stuck on a white screen until the page was refreshed. This issue has been resolved. |
Server |
N/A |
Version 21.1.323 (Service Pack)
Issue |
Area |
Description |
Required Update |
Sensor OS |
|---|---|---|---|---|
CYBR-48379 |
Investigation |
On the Investigation screen, if you run a query on the Machine element, in the Results Grid, the column Active users (which did not contain any data) is no longer displayed by default. |
Server |
N/A |
CYBR-48418 |
NGAV |
Signature-based On demand scans are now available on machines running CentOS 6. |
Sensor and server |
Linux |
CYBR-47215 |
OS Support |
You can now install sensors on machines running the Debian 10 operating system. |
Sensor and server |
Linux |
CYBR-48818 |
OS Support |
You can now install sensors on machines running the macOS Monterey operating system. The macOS Endpoint Security Framework (ESF) is not currently supported. |
Sensor and server |
macOS |
CYBR-48695 |
Sensor Dashboard |
On the System > Dashboard screen, machines running Windows 11 are now displayed under the Sensors by OS version section. |
Server |
N/A |
CYBR-47812 |
Sensor Management |
We have made improvements to how the Active Console process (ActiveConsole.exe) manages the Minion Host process. |
Sensor and server |
Windows |
CYBR-47503 |
Sensor Management |
We have made improvements to the communication pipe between the Active Console (ActiveConsole.exe) and the Minion Host processes. |
Sensor and server |
Windows |
CYBR-40110 |
Device Control |
On machines running Windows 7 or Windows 10, with end users notifications enabled and Device control enabled with USB mode set to Block, if a USB device was used with the machine, no end user notification was displayed. This issue has been resolved. |
Sensor and server |
Windows |
CYBR-48380 |
Investigation |
On the Investigation screen, if you ran a query using the Scheduled task element and edited the columns in the results grid, the Scheduled task column was removed from the results grid and was unable to be re-added. This issue has been resolved. |
Server |
N/A |
CYBR-48846 |
Sensor Management |
On the System > Sensors screen, if you tag sensors by importing the CSV file template, the tags were not applied to the sensors correctly. This issue has been resolved. |
Server |
N/A |
CYBR-48481 |
Sensor Management |
On the System > Sensors screen, if you exported a list of sensors containing a single sensor to a CSV file, the CSV file was missing fields. This issue has been resolved. |
Server |
N/A |
CYBR-47368 |
Sensor Management |
If you installed a sensor on a machine running Amazon Linux 2, an installation error was received. This issue has been resolved. |
Sensor and server |
Linux |
CYBR-48277 |
Sensor Management |
The Archived sensor report email notification contained the number of sensors that were already archived and not the number of sensors to be archived. This issue has been resolved. |
Server |
N/A |
Version 21.1.301 (Service Pack)
Issue |
Area |
Description |
Required Update |
Sensor OS |
|---|---|---|---|---|
CYBR-48695 |
Sensor Dashboard |
On the System > Dashboard screen, machines running Windows 11 are now displayed under the Sensors by OS version section. |
Server |
N/A |
CYBR-40644 |
Sensor Management |
After initial installation, the sensor now reports to the Windows Security Center after the signatures database download is complete. This prevents an unnecessary notification stating virus protection is out of date. If after 4 hours the signatures database download is not complete, the notification stating virus protection is out of date is correctly displayed. |
Sensor and server |
Windows |
CYBR-48349 |
Malop Management |
If you updated a Malop after it was closed, the update was excluded from email notifications. This issue has been resolved. |
Server |
N/A |
CYBR-48124 |
Malop Management |
In version 21.1.281, on the Malop details screen, the Mark as active button did not classify the Malop as active. This issue has been resolved. |
Server |
N/A |
Feature |
Description |
Required Update |
Sensor OS |
|---|---|---|---|
Fileless protection |
In addition to the Cybereason platform’s existing PowerShell and .NET protection modules, the Cybereason platform now integrates with Microsoft Anti-Malware Scan Interface (AMSI) to complete its Fileless protection suite. Learn more. |
Sensor |
Windows |
OS support |
We now support sensors running on SLES 15 machines, with specific limitations. |
Server |
Linux |
Investigation |
On the Investigation screen, an estimated count of query results is now displayed instead of the total count. This change is applies to the Elements that appear in the Investigation screen as well as the query results. |
Server |
N/A |
Linux SLES 15 support |
On the Dashboard screen, machines running Linux SLES 15 are now displayed under the Sensors by OS version section. |
Sensor |
Linux SLES 15 |
Process data collection |
We have updated the configuration for process collection on the sensor to uses more data points to help better determine the process name. and ensure the platform identifies the correct process name for a process. |
Sensor |
Windows |
Version 21.1.243
Feature |
Description |
Required Update |
Sensor OS |
|---|---|---|---|
Behavioral allowlisting |
You can specify sensor groups when building Behavioral Allowlisting rules. Adding the sensor group filter to the Owner Machine Element in a Behavioral Allowlisting rule ensure the rule only applies to sensors in the specified group. Learn more |
Server |
N/A |
Endpoint Protection exclusions |
To improve the use of EPP exclusions (such as Anti-Malware exclusions) and minimize negative effects on endpoint machines, we have updated the platform’s exclusion configuration to properly address wildcard characters. |
Sensor |
Windows |
Sensor CSV export |
Previoudly, when exporting sensor data from the UI, the resulting CSV file would be incorrectly formatted if a sensor field included a new line character (n). This is has been resolved. |
Server |
N/A |
Version 21.1.223
Feature |
Description |
Required Update |
Sensor OS |
|---|---|---|---|
Investigation query filters |
Analysts can narrow down the results of an on-going query by selecting individual values from the results to add to the query filter. Learn more |
Server |
N/A |
Device Control |
To streamline device management, you can now upload a list of USB devices using a CSV file. We have also renamed the Device control > Device control exclusions section to Manage devices to reflect the various settings you can update using this area. Learn more Note This version introduces the first iteration of the Device control CSV capability. While you can currently add up to 50 USB devices via the CSV file, we are working to increase this amount in the next release. |
Server |
N/A |
Version 21.1.204
Feature |
Description |
Required Update |
Sensor OS |
|---|---|---|---|
Malops management |
We have made the following improvements to the Malops management screen:
|
Server |
N/A |
Anti-Malware exclusions |
To improve performance, you can now exclude files from Anti-Malware based on the name of the process that opens the files. We have also excluded known and safe processes by default. Learn more |
Sensor |
Mac OS |
Device Control |
To allow protection for USB storage devices on additional operating systems, the Device control feature is now supported on endpoints running Linux operating systems. |
Sensor and Server |
Linux |
Investigation query limits |
On environments with the newer data infrastructure enabled, on the Investigation screen, the default limit of the Limit results slider can now be configured per environment. |
Server |
N/A |
Version 21.1.182
Feature |
Description |
Required Update |
Sensor OS |
|---|---|---|---|
Sensor viewer role |
User administrators can now assign the ‘Sensor viewer’ role to users who need read access to certain sensor groups. Learn more. |
Server |
N/A |
Sensor Groups |
A new column, Group Assignment, was added to the System > Sensors screen. The Group Assignment column indicates whether a specific sensor was added to a group by assignment logic (‘Dynamic’) or manually (‘Manual’) |
Server |
N/A |
Malop Notification emails |
Sensor admin L1 users will now receive emails when sensors in their assigned groups are archived. |
Server |
N/A |
Device Control |
To increase the control and protection for devices in your organization, you can now block USB devices of various types, in addition to USB mass storage and MTP devices. Learn more. |
Sensor,server |
Windows |
File search permissions |
Beginning in this release, you no longer need Technical Support to enable access to the File search screen. You only need to assign a user the Responder L1 or Responder L2 role. Learn more |
Server |
N/A |
Version 21.1.144
Note
Linux AV is generally available in version 21.1.144 and later. When you upgrade a Linux sensor to this version, and the sensor is assigned a policy with Anti-Malware > Signatures mode enabled, scheduled and on demand scans run automatically according to policy settings. On access scans on Linux machines are enabled by default in version 20.2.462 and later (prior to this version, contact Technical Support to enable on access scans).
Feature |
Description |
Required Update |
Sensor OS |
|---|---|---|---|
Password policy |
Beginning with version 21.1.143, new environments will have the following default password policy settings:
|
Server |
N/A |
Linux AV |
Scheduled and on demand Signature-based scans are now generally available on machines running Linux sensors. When working with a Linux sensor that is assigned a policy with Anti-Malware > Signatures mode enabled, scheduled and on demand scans run automatically according to policy settings. On access scans are not currently supported. |
Sensor |
Linux |
Behavioral document protection |
We have adjusted the detection logic for evidence, suspicions, and Malops related to Behavioral document protection to ensure that the evidence, suspicions, and Malops are generated correctly with accurate results. |
Server |
N/A |
Version 21.1.121
Version 21.1.103
Feature |
Description |
Required Update |
Sensor OS |
|---|---|---|---|
Query operators |
We have added additional operators for Enum type features to help you better perform investigation queries:
|
Server |
N/A |
Device control |
To increase your organization’s ability to protect various device types, the Cybereason platform now supports Media Transfer Protocol (MTP) devices, which refer to mobile and media devices. You can configure the settings for mobile/media devices and also exclude these devices in the System > Sensor policy > Create/Edit policy> Endpoint controls >Device control section. Learn more |
Server |
Windows/Mobile (both iOS and Android) |
Machine isolation |
You can now isolate Linux machines using the machine isolation feature. For more information, see Response features. |
Sensor |
Linux |
Cybereason system tray icon |
We have updated the Cybereason system tray icon from blue to white. For more information about the system tray icon and notifications, see Endpoint Machine Notifications and Desktop Settings. |
Sensor |
Windows |
Version 21.1.81
Feature |
Description |
Required Update |
Sensor OS |
|---|---|---|---|
Incident response |
You can now deploy, run, and collect results for third-party incident response tools using the Cybereason platform. You request a special environment for Incident Response, upload and deploy tool packages, run the tool, and retrieve the results to upload them to a pre-defined GCP bucket. Learn more |
Server |
Windows |
Version 21.1.62
Feature |
Description |
Required Update |
Sensor OS |
|---|---|---|---|
Device Control modes |
The Device control feature can now be enabled in one of three modes:
Note If you set the Device control mode to Read only on a sensor that has not yet been upgraded to the latest version, the Cybereason platform automatically changes the mode to Monitor. |
Server |
Windows |
Sensor grouping for analysts |
System and user administrators can now assign the Local analyst L1 or L2 role to analysts that will interact with sensors in specific sensor groups. L1 and L2 Local analysts can perform investigations on data from sensors in their assigned groups. L2 Local analysts can remediate Malops associated with sensors in their assigned groups. Learn more. Note This feature requires that your Cybereason instance uses the newer data infrastructure. |
Server |
N/A |
MITRE technique tags |
You can now identify the MITRE tactics and techniques for an evidence or suspicion with a special tag indicating the tactic or technique number. Learn more |
Server |
N/A |
Version 21.1.23
Feature |
Description |
Required Update |
Sensor OS |
|---|---|---|---|
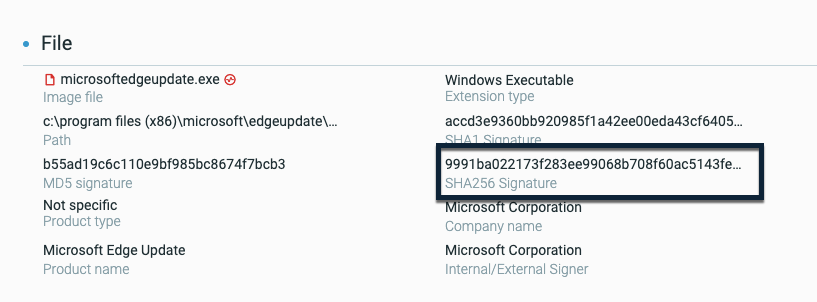
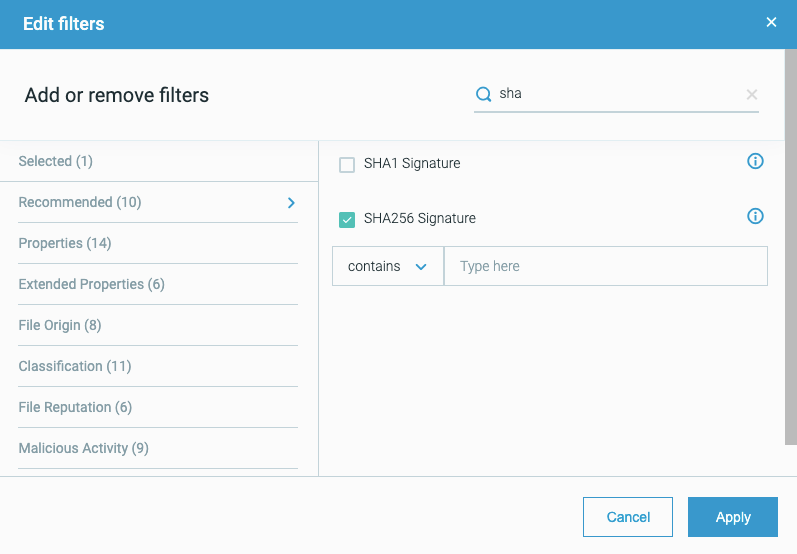
SHA-256 support |
The Cybereason platform now supports the collection of SHA-256 file hash values by the sensor, and the detection of malicious activity based on SHA-256 file hash values. You can see details on the SHA-256 file hash values as part of the Element Details for a file: You can also search for files based on the SHA-256 file hash value: |
Server and Sensor |
Windows |
Certificate updates
As of version 20.1.222, the Cybereason sensor obtains the GeoTrust RSA CA 2018 Intermediate CA directly from the server.
If you upgrade from versions earlier than 18.1 to this version and receive a “Certificate chain trust error” message, do one of the following:
Upgrade to the latest version.
Manually resolve the issue. For more information, see "Certificate Chain Trust Error" Message after Sensor is Installed on a Windows Machine.
For more information on working with certificates, see TLS Communication.
Please see our Legal Disclaimer on links to third party websites.