23.2 Version Highlights
Cybereason version 23.2 LTS introduces new features, including the unified policy exclusions screen, Sensor Actions screen, Sensor Tampering Protection GA, and many more.
In this topic:
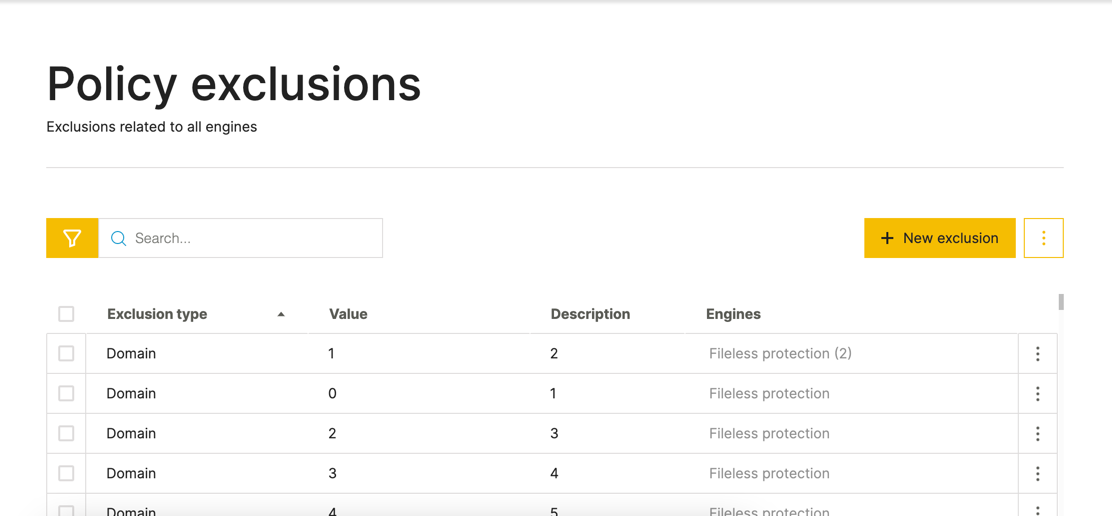
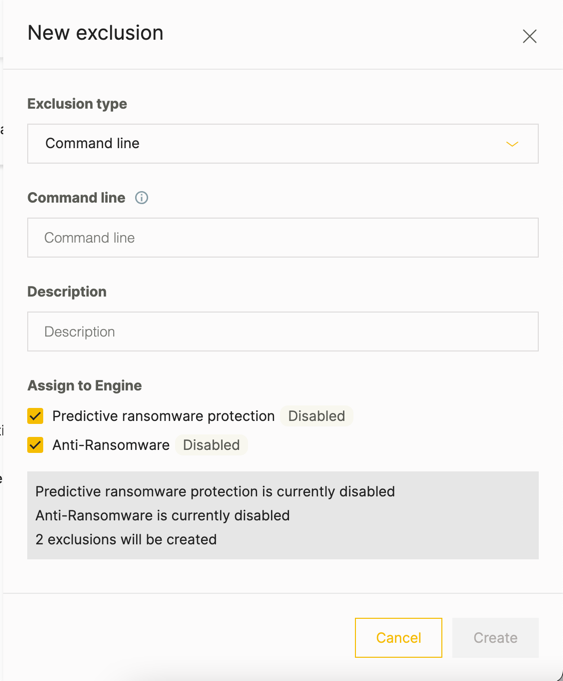
Unified policy exclusions screen
To help you streamline the process of adding exclusions for different NGAV protection engines, you can now use the Policy exclusions screen in a sensor policy. You can use the Policy exclusions screen to add all exclusions in a single place, based on the type of item to exclude, such as a process, file, and so forth.
The Policy exclusions screen also guides you on the types of exclusions you can add and the relevant protection engine for these exclusions.
You can also create exclusions in this screen by importing a CSV file with the exclusions.
When you add the exclusions in this screen, the exclusions are also added in the other respective screen for the protection engine.
For details, see Add Exclusions from NGAV Protection.
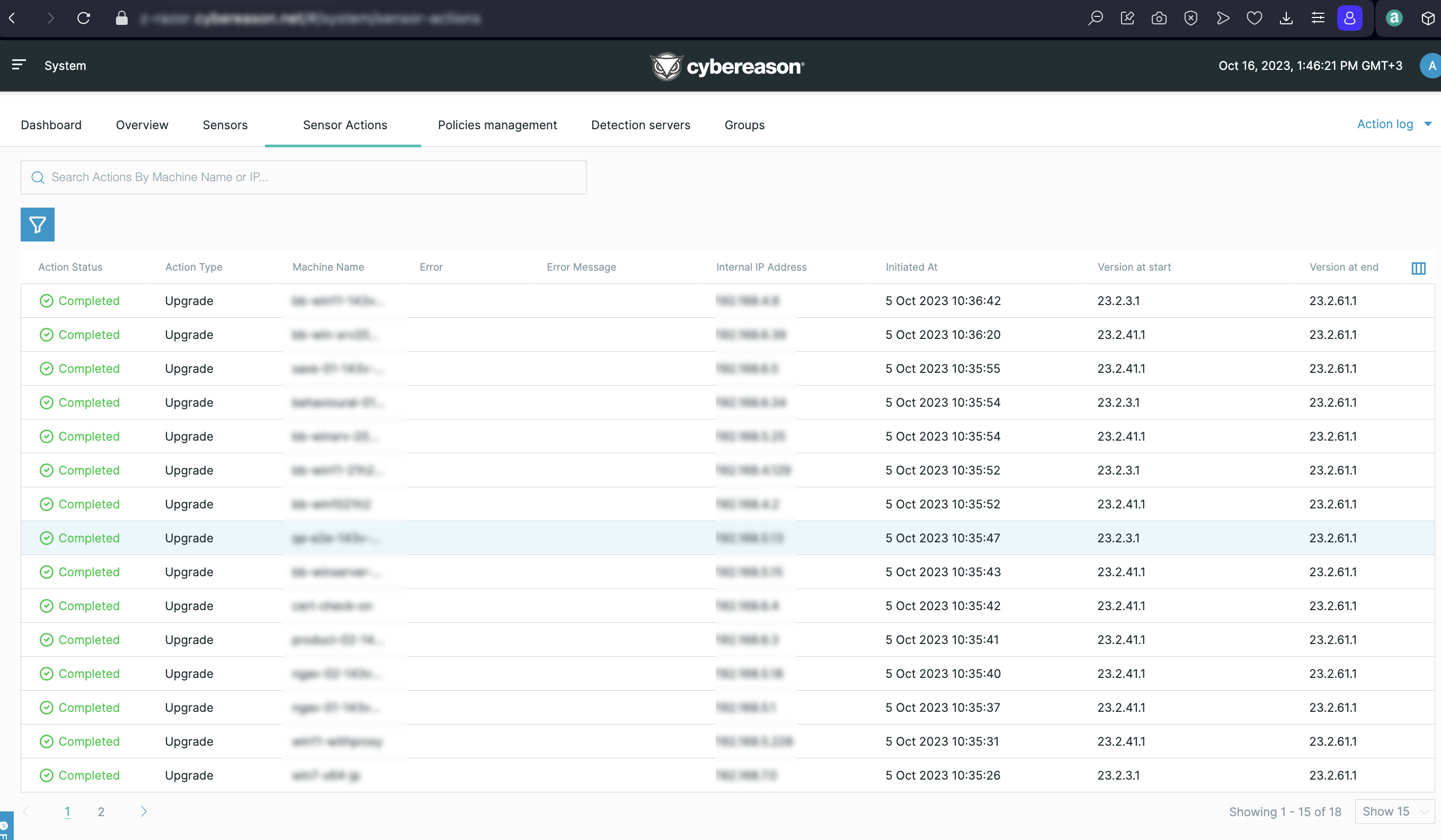
Sensor actions screen
You can now use the Sensor actions screen to view and monitor the results of essential sensor actions such as a sensor upgrade, installation, or uninstall.
For details, see Monitor Sensor Actions.
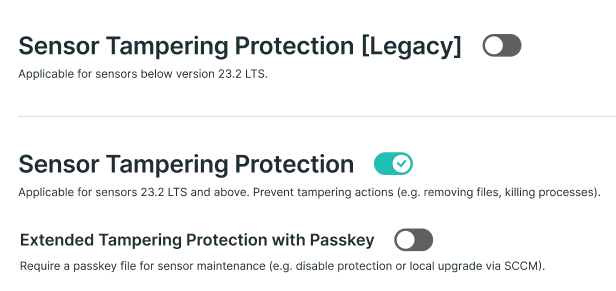
Sensor Tampering Protection available
The Sensor Tampering Protection feature for endpoint machine sensors introduced in previous Cybereason versions is now generally available.
Sensor Tampering Protection provides enhanced protection for the sensor running on Windows endpoints, through protection of the sensor processes, files, services, and registry entries against unauthorized or malicious modifications or kill attempts. In addition, Sensor Tampering Protection protects the sensor from unintentional end user actions that may compromise the sensor’s security, such as killing a resource-intensive sensor process.
For details, see Use Sensor Tampering Protection.
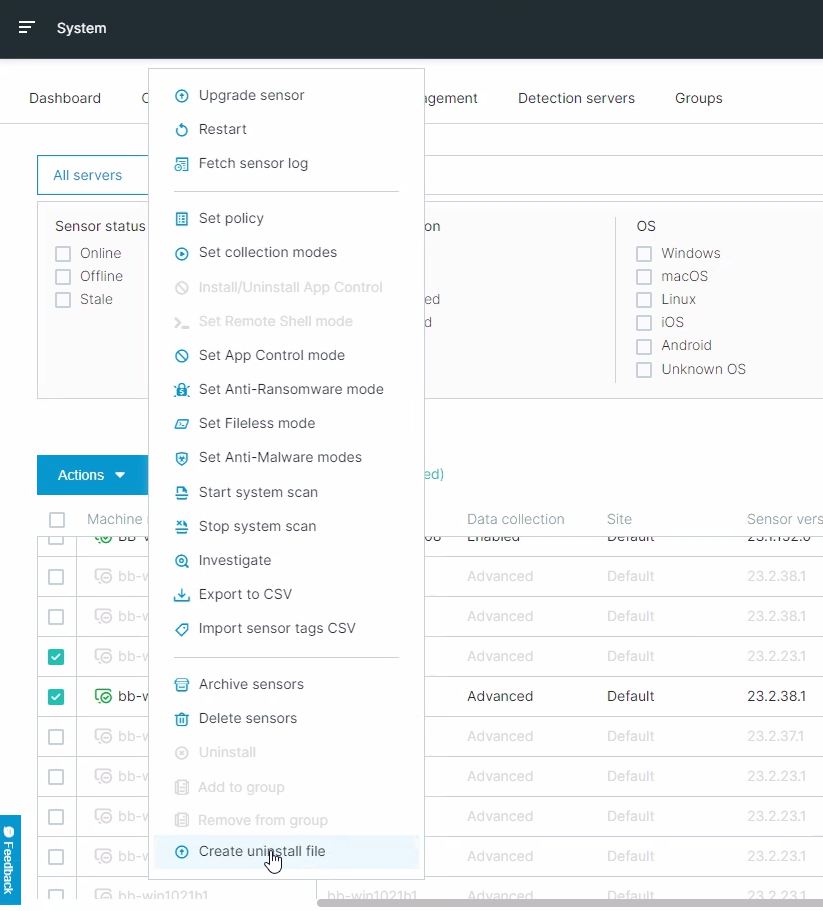
Uninstall sensors with an uninstall file
To help you manage the sensor uninstall process without the need to save or remember uninstall password, you are now able to generate an uninstall file for a sensor in the Sensors screen. After you generate the file, you send this file to the endpoint machine user and run the file, which uninstalls the snesor without an uninstall password.
For details, see Uninstall using an uninstall file.
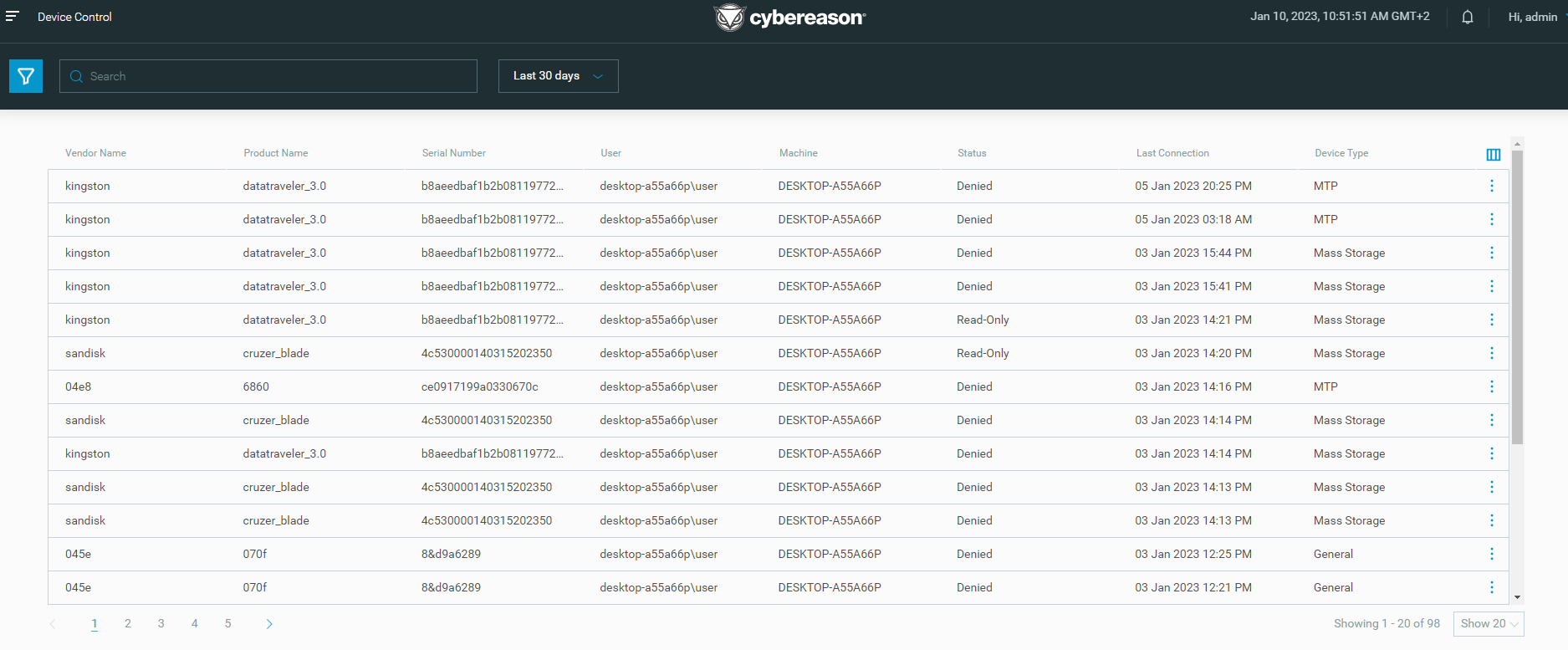
Device Control screen available
Beginning in this version, the Device Control screen is available by default without the need to enable this screen with Technical Support. In the Device Control screen, you view Device Control events and easily monitor the usage of USB devices across the environment.
For details, see View Device Control events and monitor USB usage.
Scaled sensor upgrade available
The scaled sensor upgrade process introduced in previous Cybereason versions is now available by default without the need to enable this feature with Technical Support. In this scaled upgrade process, the sensor checks for an updated sensor installation package every 10 minutes and downloads the new package when it is available. Then, when the system administrator triggers the upgrade in the Sensors screen, the machine automatically installs the new package without waiting for the downloade first.
For details, see Scaled Sensor Upgrade Process - FAQ.
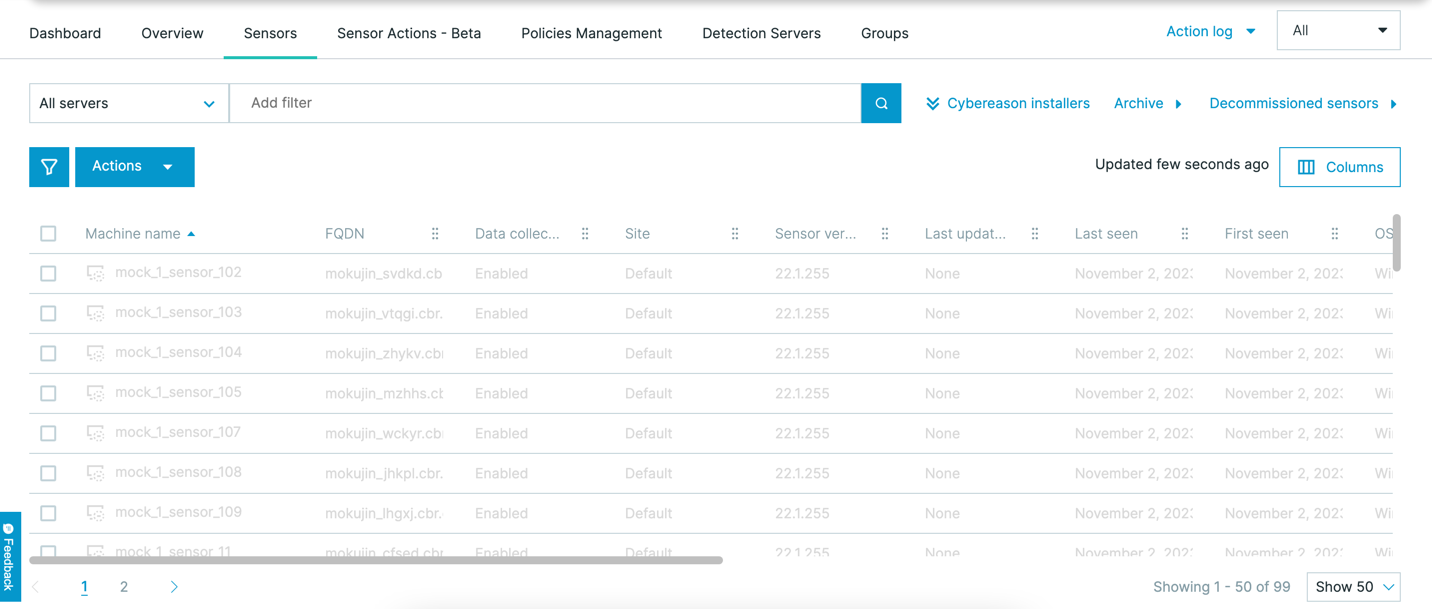
Updated Sensors screen
Note
The updated Sensors screen is not available by default. Contact your Customer Success Manager to gain access to this screen.
In this version, you can use an updated version of the Sensors screen to help you manage sensors.
The updated version moves the quick filters to the left of the sensors table, enabling you to see additional sensors in the sensors table. The same filter criteria are still available through the search bar.
You can still perform common sensor actions through the Actions menu.
For details, see Monitor and Manage Sensors.
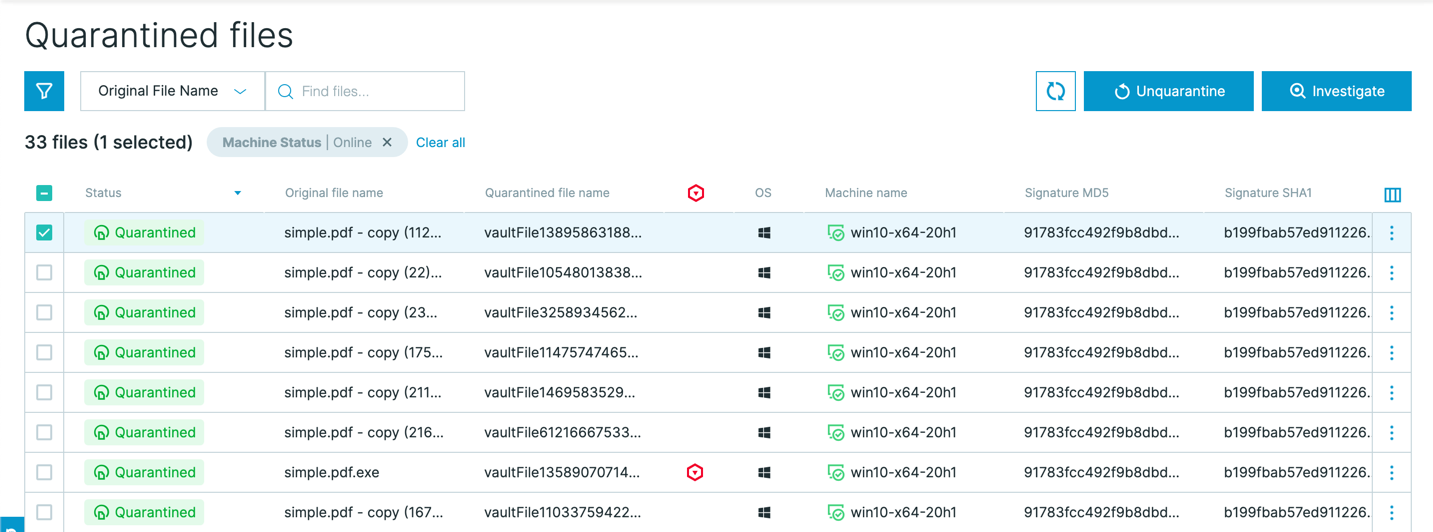
Quarantined files screen
Note
The Quarantined Files screen is not available by default. Contact your Customer Success Manager to gain access to this screen.
To help you with the process of removing quarantined files from quarantine in the event of false positive detections, you can us the Quarantined Files screen. This screen displays all files that the Cybereason platform has placed in quarantine (depending on automatic or manual response actions). You can view details about these files, but also unquarantine one, many, or all quarantine files in a single operation.
For details, see Unquarantine a file from the Quarantine Files screen.
Additional features on Mac and Linux machines
To provide additional levels of security for macOS and Linux machines, we have extended the support for many existing features to machines running supported versions of the macOS and Linux operating systems:
On macOS, you can see a Cybereason system tray icon.
You can uninstall macOS and Linux sensors from the Sensors screen in addition to sensors on Windows machines.
Live File Search is available on both macOS and Linux machines.
Note
Live File Search is not available by default on macOS machines. Open a Technical Support case to enable file searches on macOS machines.
You can use Variant Payload Protection (EA) on Linux machines.
We now collect information on loaded modules on macOS machines.
Improvements for MalOps management
We have added a number of improvements to the MalOps management screen to help you better manage the MalOp workflow.
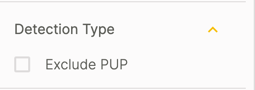
You can use the Detection type filter to display MalOps classified as Potentially Unwnted Programs.
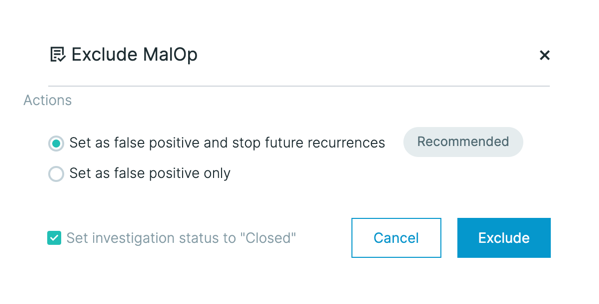
In a specific MalOp, we have expanded the number of actions available to take when excluding a MalOp from future detection.
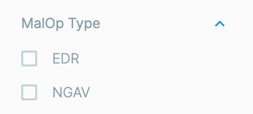
To help you more efficiently filter different types of MalOps, you can use the MalOp type filter to select either EDR (AI Hunting) and NGAV (Endpoint Protection) MalOps.
For details, see View MalOps with the Data Platform Architecture.
Improved capabilities for behavioral allowlisting rules
To help you create more relevant behavioral allowlisting rules, we have added the following capabilities to the behavioral allowlisting process.
You can now use the Parent Process and Grandparent Process Elements when creating the rule logic.
You can use the starts with and ends with operators for the Command line Feature to help you create rule logic based on the beginning or ending of a specific command line string.
You can now use special characters in the rule syntax.
For details, see Manage Behavioral Allowlisting Rules.
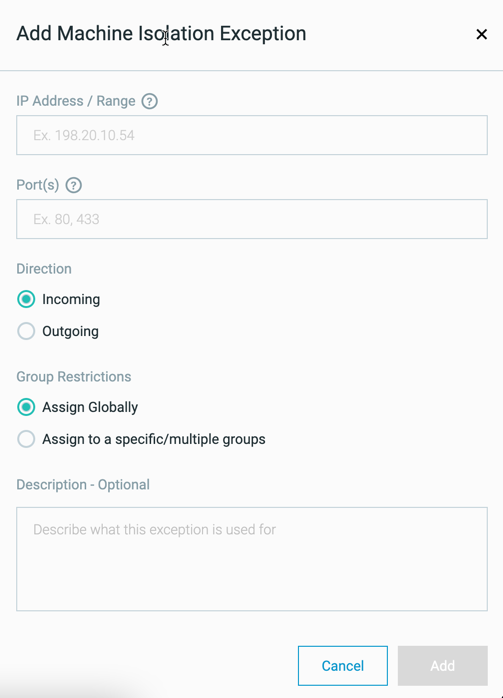
Machine isolation exception rules for sensor groups
When creating a machine isolation exception rule, if you have enabled sensor grouping in your environment, you have the ability to which groups this exception applies.
For details, see Define isolation exception rules.
Improved Windows process collection
To improve the collection of process information on Windows machines, we have updated the collection of data for the Windows sensor:
Process information is now collected using the sensor’s driver which helps improve the time details of the process.
In addition, the sensor also collects details in the standard input or output for a process.
New operating systems
In this version, we have added support for the following architectures, frameworks, or operating systems:
FIPS on Windows sensors
Windows AM-PPM
SNI
EA availability for sensors on Linux ARM machines