22.1 Version Highlights
Cybereason version 22.1 LTS introduces new features, including SHA-1/SHA-256-based prevention, Remote uninstall of Windows sensor, the Machine Timeline and IR tools screens, and more.
In this topic:
SHA-1 and SHA-256 based prevention
You can now prevent the execution of SHA-1 and SHA-256 file hash values with Application Control. Add these values to your environment’s blocklist and the Cbyereason platform will block execution of those files.
For details on using Application Control, see Prevent File Execution with Application Control. For details on how to use the allowlist and blocklist, see Manage Reputations.
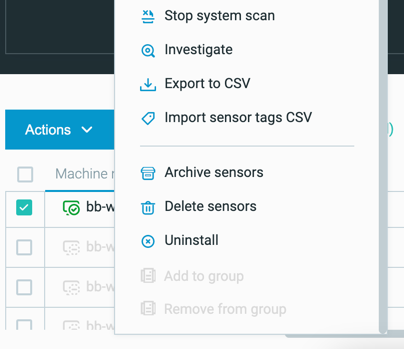
Remote Uninstall Sensors (for Windows)
Now, if you need to uninstall a sensor from the machine, such as when you do not have access to the machine, you can run the uninstallation directly from the Cybereason platform Sensors screen:
For more details, see Uninstall sensors from the Sensors screen.
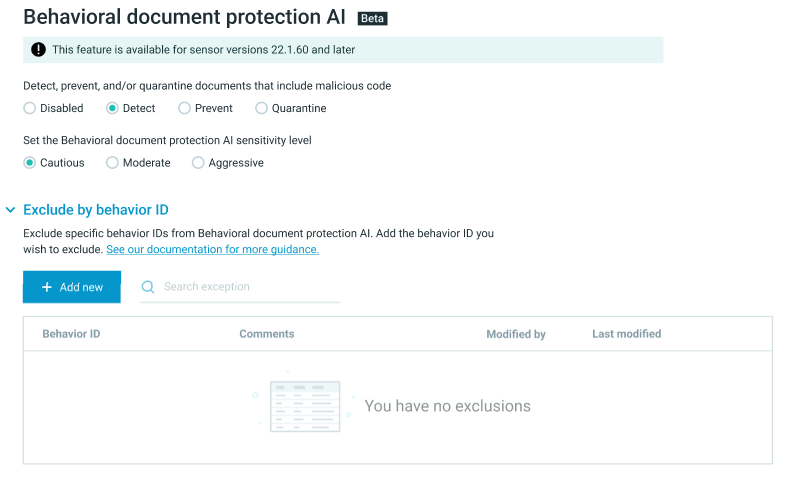
Behavioral Document Protection AI mode
Note
Behavioral Documentation Protection AI mode is not generally available. To gain access to this feature, contact your Customer Success Manager.
This version introduces Behavioral Document Protection (BDP) AI as part of the NGAV protection suite. BDP AI utilizes a machine learning algorithm to analze documents to identify if they contain malicious macros.
For details, see Behavioral Document Protection AI.
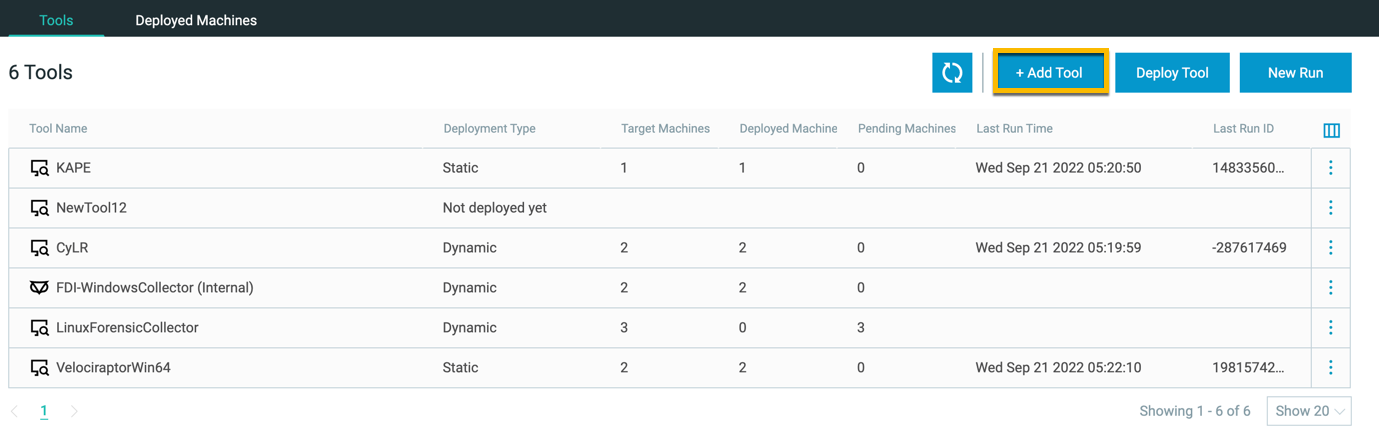
Manage incident response and forensic tools from the platform with the IR Tools screen
Note
To use this feature, you must add the DFIR package to your Cybereason environment. To add this package, contact your Customer Success Manager.
Previously, when you wanted to deploy or run incident response (IR) or forensic data ingestion (FDI) tools through your Cybereason platform, you were required to use the API to perform these operations.
Now, in the IR Tools screen, you can upload, deploy, run, and collect results from any IR or FDI tool without the need to use API requests or scripts. While the API for IR and FDI tool management is still available, the IR Tools screen provides a more intuitive way to manage your IR and FDI tool operations.
For details on the IR Tools screen, see Manage Incident Response and Forensic Data Ingestion Tools with the Platform.
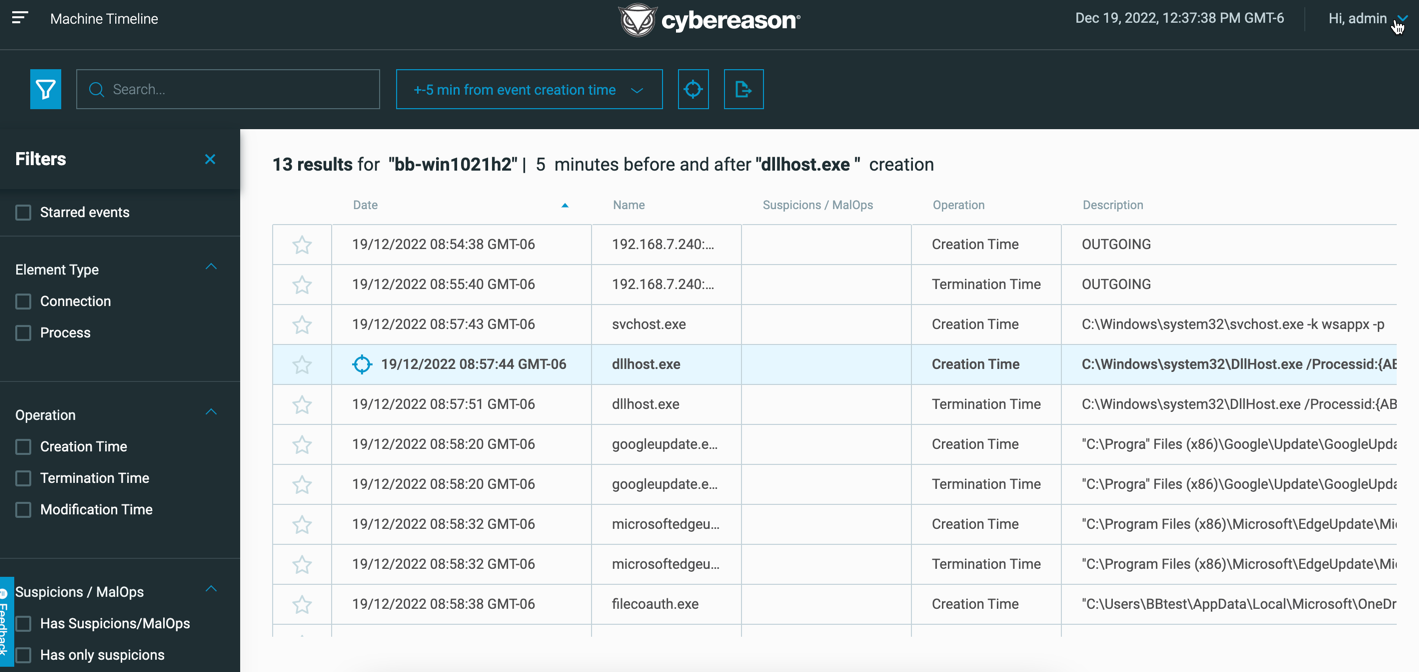
Machine timeline screen
If your Cybereason environment uses the new Data Platform, you can now use the Machine Timeline screen:
The Machine Timeline screen helps you:
Quickly view detailed information for a specific machine for related activity, such as processes, connections, or files, within a specific time frame before and after process execution
Uncover new indicators of compromise through seeing the activity on a machine around the time of the item’s detection
Determine whether a machine requires deeper forensic analysis.
For details, see Machine Timeline.
Monitor sensor upgrades
To help you better perform sensor upgrades, the sensor upgrade program now runs a number of prerequisite checks in the background on the machine to ensure that the machine on which you are upgrading the sensor meets the requirements for the sensor version.
In addition, after the prerequisite checks finish, and during or after the upgrade process, you can monitor all the results of the prerequisite checks (if there is a failure) and the upgrade process.
For details, see Monitor Upgrade Process.
Variant Payload Protection (VPP) general availability
The Variant Payload Protection (previously called Binary Similarity Analysis in-memory protection) is now generally available as part of your Behavioral Execution Prevention protection.
For details, see Variant payload protection.
Device control for macOS
Device Control is now supported on machines running supported macOS versions.
For details on Device Control, see Device Control.
Perform Anti-Malware scans from an endpoint machine
To help provide more timely Anti-Malware protection on machines, you can run scans from an endpoint machine:
Run a scan, on-demand, through a right-click option on a folder
Run a scan from the command line
For details, see On Demand Scans.
File events and registry events collection configuration improvements
The File events and Registry events collection configuration has been updated to simplify the process to use these collections.
Both collections are available by default, so you no longer need to contact Technical Support to enable these options in your environment.
In addition, for the File events collection, the collection is now limited to files of certain types related to security needs. This helps you limit the data load on your Cybereason platform’s servers.
For details on how to configure file events and registry events collections, see Configure Additional Endpoint Data Collections.
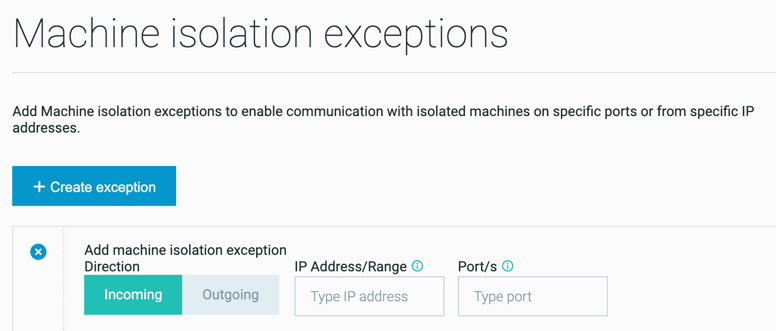
Machine isolation rules for IP ranges
When you create a machine isolation exception rule, you can now add IP ranges instead of a single IP address:
For details, see Define Isolation Exception Rules.
Investigation query usability improvements
If your Cybereason environment uses the new Data Platform, to help make your investigation queries and results more useful and represent more accurate information, we added a number of improvements.
When you build a query, if you have multiple values for the selected filter Feature in your query, you can join the values with the AND operator. For example, you can add Command line contains abc AND Command line does not contain xyz to the same filter to return items whose command line contains the string abc but not the string xyz.
Lastly, the timeline filter (created on/existed on) located in the top right of the Investigation screen is now applied to all Elements in the query chain that have time-based components (such as Connection, Logon Session, Detection Events, Malop Process, and Process), instead of the last Element in the query chain.
For details on the operator changes, see Understanding query parts.
System Viewer role
To provide greater visibility for your administrators but also limit the number of users that can edit system settings, we have aded a new System Viewer user role. Users with the System Viewer role have read-only permissions for screens to which the users with the System admin role have access. While users with the System viewer role can view the Cybereason platform’s system and sensor settings, they cannot change any settings or perform actions.
For details on the System Viewer role and other roles, see User roles.
Remote Shell on Mac and Linux
Use of the Remote Shell utility is now supported on machines running supported macOS and Linux versions.
For details on the Remote Shell utility, see Respond to Threats on a Machine with the Remote Shell.
Sectigo code signing for Windows sensors
Sensor binary files for Windows machines are now signed by Sectigo cross certificates to meet MVI (Microsoft’s virus initiative) requirements.
Note
Windows 7 machines are no longer supported with the Sectigo code signing sensor binary files.
Mac and Linux sensor collection improvements
We have added new frameworks for collection on Mac and Linux sensors:
Support for the Endpoint Security Framework (ESF) on macOS machines
Availability of the eBPF collection framework on specific versions of Linux
Note
The eBPF framework on Linux machines is not generally available. Contact your Customer Success Manager to gain access to this feature.
File search for environments with sensor grouping
If your Cybereason environment uses sensor grouping, you can now use the Live File Search screen if your Cybereason user has the Local responder role and is assigned to sensor groups. The results that display for the search operation only display relevant results from sensors in the assigned groups for your users.
For details on file search, see Search for Files on Machines.
New OS support
We have added support for the following operating systems in this version:
Windows 10 22H2
Windows 11 22H2
macOS Monterey 12.3 - 12.6
macOS Ventura
Apple Silicon Mac native (M2), M2 Max, and M2 Pro
Rocky Linux 8
Ubuntu 22.04
RHEL 9
Obfuscate log entries with sensor policy exclusions
In the sensor logs, sensor policy exclusions for NGAV settings are obfuscated so that attackers can no longer use this information to find weak points in a machine’s protection.