21.2 Version Highlights
Cybereason version 21.2 LTS introduces new features, including Cybereason XDR, Cloud Workload Protecion, Behavioral Execution Prevention, and many more.
In this topic:
XDR and Cybereason Connect
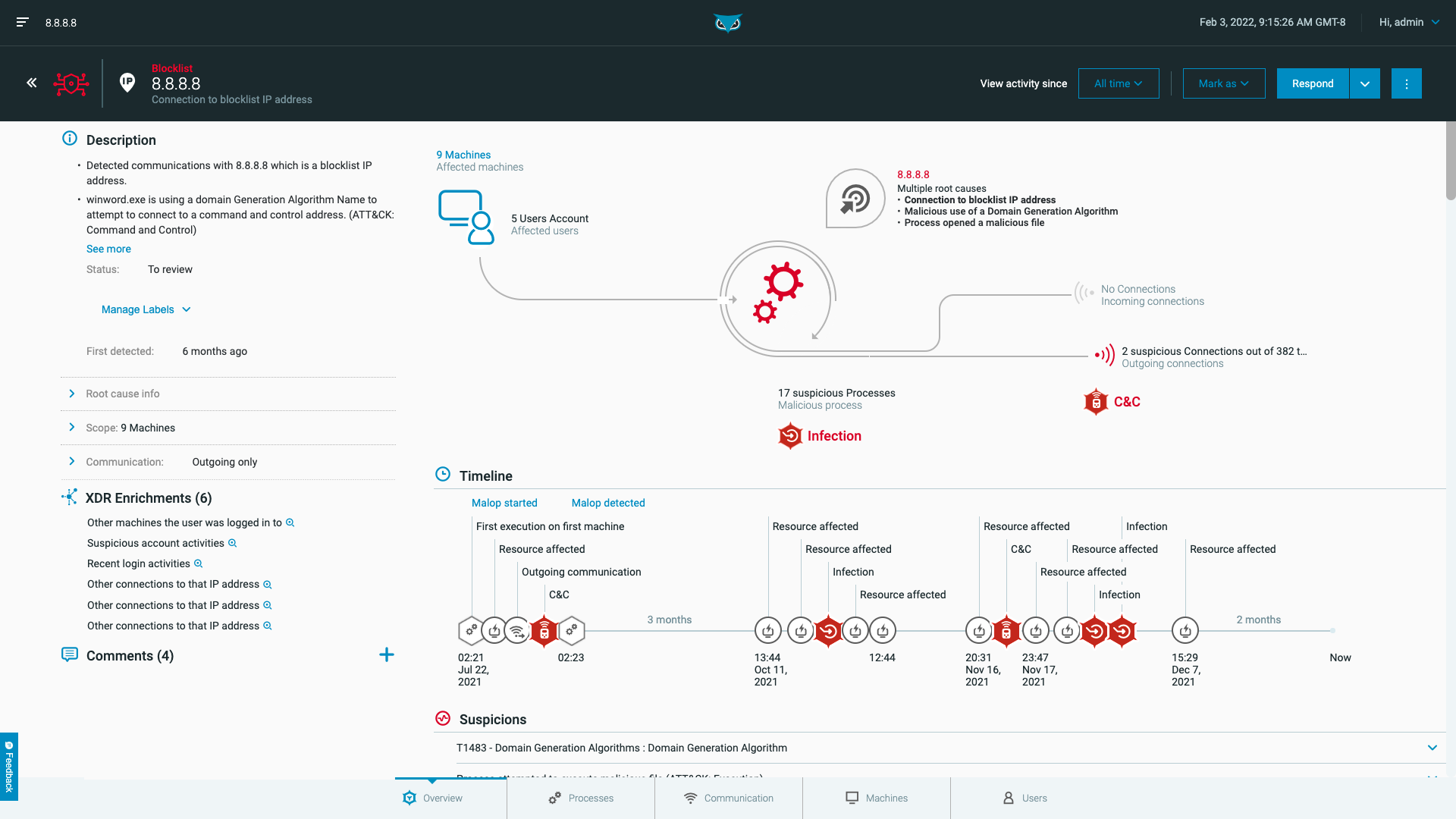
With this version, you can use the Cybereason XDR module as part of your Cybereason platform.
Cybereason XDR enables you to retrieve data from your identity, workspace & network data sources to identify blind spots in your attack surfaces, get high fidelity attack stories without the need to chase down individual alerts.
Cybereason XDR enables you to retrieve log source data from numerous supported integrations. Using an integrated Google Chronicle data lake instance, Cybereason XDR retrieves log source data from the other integrated platforms, parses the log source data, and imports the parsed data into the Cybereason platform.
The Cybereason platform then correlates XDR log source data with existing data from other existing data to enable you to view potential malicious activity from even more sources.
You manage all Cybereason XDR log source integrations from the new Cybereason Connect screen.
For details:
Extended Detection and Response (XDR) about Cybereason XDR
Learn more about Cybereason Connect
Cloud Workload Protection (CWP)
Cloud Workload Protection provides deep visibility into the runtime of containerized platforms, providing unified protection, detection, and response across containers.
Cybereason has developed two new sensors that can be deployed on a Docker host or Kubernetes clusters. These sensors collect security data that is correlated with all other data collected by Cybereason and is displayed across the Cybereason platform.
Note
CWP is available on a limited basis. To use CWP, contact your Customer Success Manager.
Behavioral execution prevention
Behavioral execution protection allows organizations to detect and prevent malicious execution of processes based on the process behavior. Behavioral execution protection uses intricate research data to identify anomalies in the process creation image name, command line, image file metadata, or the process hierarchy. This data is available for inline prevention on the endpoint machines, which significantly shortens response time.
BSA in-memory protection (beta)
This version introduces Binary Similarity Analysis (BSA) protection as part of the NGAV protection suite. BSA in-memory protection performs memory scans to identify binary fractures of highly evasive attack tools (such as Cobalt strike, Emotet, Dridex, and more), and is capable of preventing these attack tools on execution. Learn more
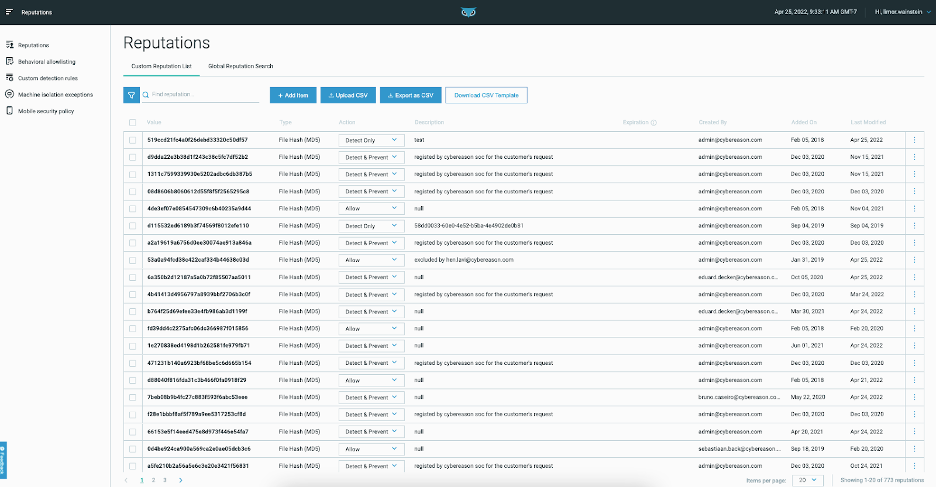
New Custom Reputations screen
In this version, the Cybereason platform updates the Reputation screen in the UI. The new Reputation screen allows you to easily add, edit, and remove custom reputations without having to use a CSV file.
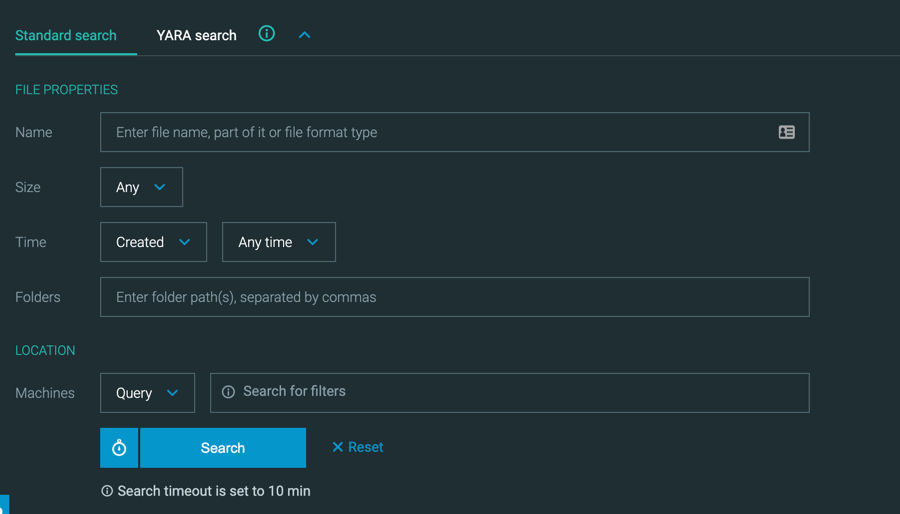
Improved Live File Search screen experience
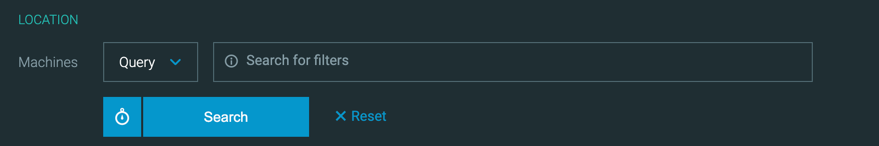
We have updated the Live File Search screen to help you perform file search operations.
Now, you can select from a standard search based on search filters, or a YARA rule-based search.
In addition, you have the option to select different types of dynamic filters to help you search the correct machines.
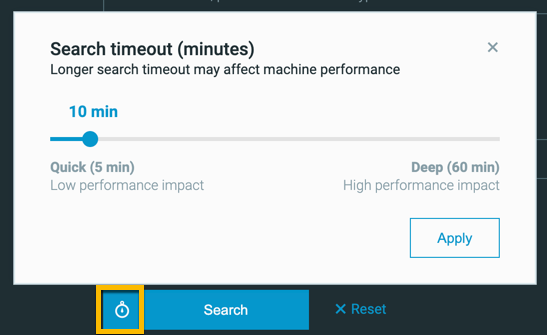
You can also set a timeout period to limit the performance effect on your platform’s servers and sensors.
Enhanced sensor tampering protection
Sensor tampering protection provides enhanced protection to the Cybereason sensor.
Phase 1 of this feature is generally available and protects sensor processes and files against unauthorized or malicious modifications or kill attempts.
Phases 2 and 3 of this feature are in a beta phase, and protect processes, files, registries and services as well as creating a MalOp if tampering activity is detected.
This feature is disabled by default. If you would like to use this feature, contact your Customer Success Manager.
Malops management removed from beta status
The Malops management screen is no longer in Beta status
Investigation query result enhancements
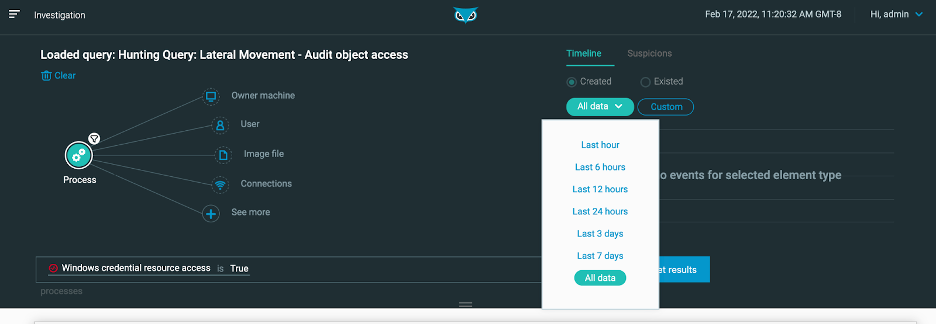
From the Investigation screen you can select a timeframe within which to apply your query. Options include the last hour, 6 hours, 12 hours, or 24 hours, the last 3 or 7 days, or all data. Default value is 24 hours.
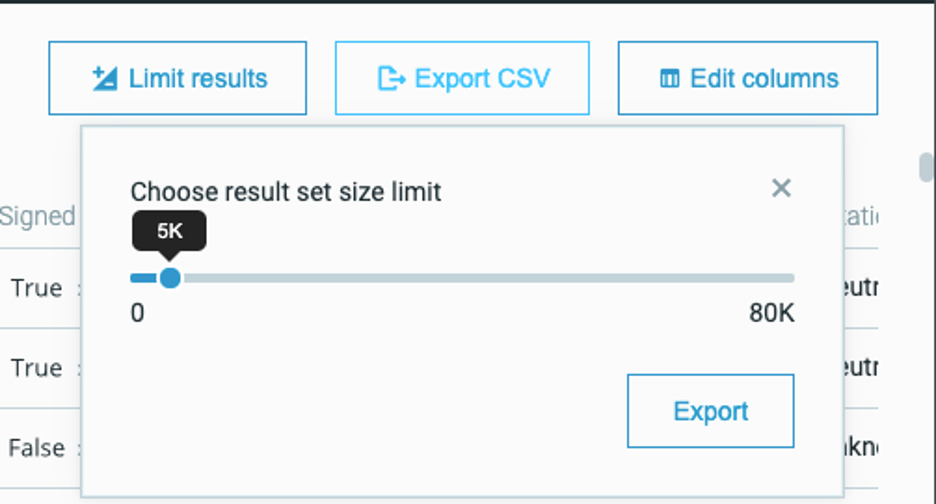
In addition, you can also now customize a specific number of results in a page of query results.
View Malop activity in a specific time frame
You can now view Malop activity from a certain time frame from the Malop details screen. Use the ‘View activity since’ feature on the top right of the Malop details screen to select a date range. The Malop details screen will update to reflect activity that occurred within the specified time frame.
Enrichment of Malop data in the Historical Data Lake
The Cybereason Historical Data Lake feature now enriches your historical queries with Malop data from your live environment. In the Create Replay screen, the Malop icon next to a machine name or process indicates how many Malops from your live environment are associated with that item.
Sensor installer packages for sensor groups
When using sensor groups you can download a sensor installation package pre-configured to add sensors to a specific group to streamline your deployment process.
Improved sensor update process
We have updated the sensor upgrade process to enable you to perform sensor updates with increased efficiency. With these improvements, you can update up to 1,000 sensors each hour.
This feature is disabled by default. To use this feature, contact your Customer Success Manager.
Expanded feature support for Linux
We have expanded support of platform features to supported Linux operating systems, including:
Support for On-file access scans
Automatic exclusion of known or safe processes on the machine
Linux AV excludes network shares and the /sys and /proc mount points from scans
Device control for MTP and USB devices
Personal firewall control
Remote Shell for Linux is also available. To enable Remote Shell on Linux machines, contact your Customer Success Manager.
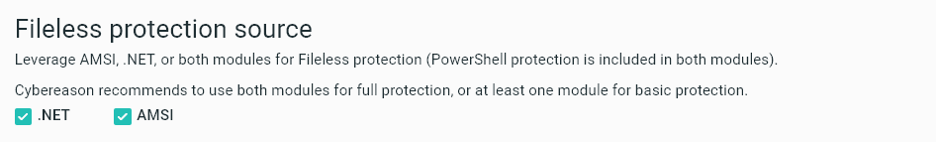
Fileless mode protection module selection
When you configure the Fileless protection settings in a sensor policy, you can choose to leverage .NET, AMSI, or both, based on the needs of your organization.
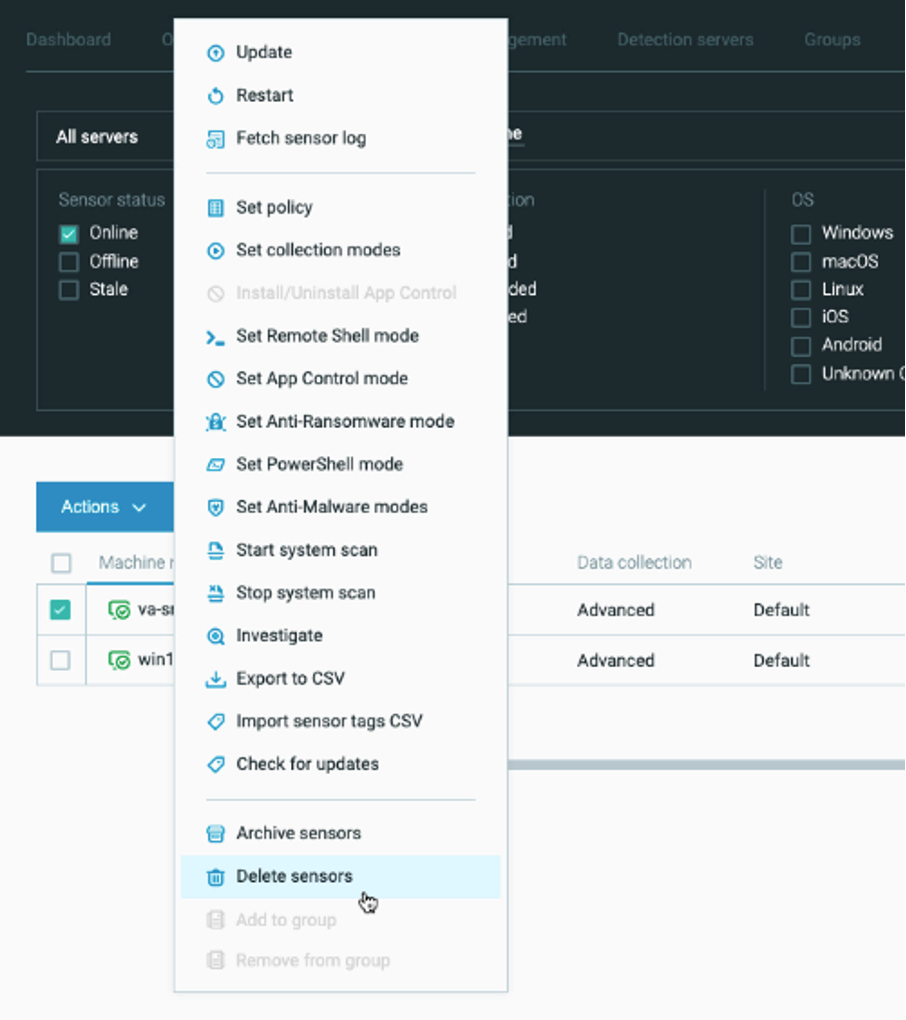
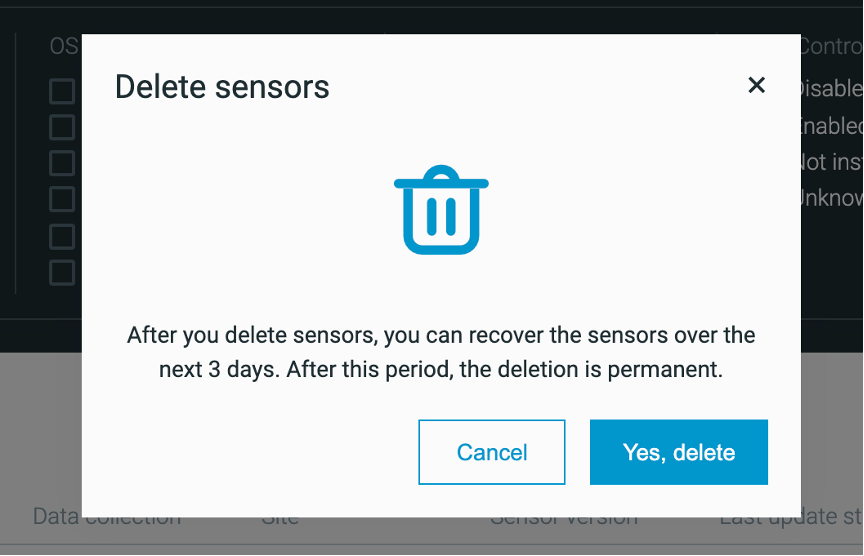
Delete sensors from the Sensors screen
To help you manage only those sensors that are used by your organization, you now have the ability to delete sensors from the list of sensors in the System > Sensors screen.
New supported platforms
We have added support for the following operating systems/platforms:
Windows 10 21H2
MacOS 12 (Monterey)
Amazon Linux 2
Debian 10