20.1 Version Highlights
Cybereason version 20.1 introduces new features, including the Malops management screen, sensor groups, integration of SSO for user identity management, and Exploit protection, as well as enhancements to several features.
Version highlights
Cybereason version 20.1 introduces new features, including the Malops management screen, sensor groups, integration of SSO for user identity management, and Exploit protection, as well as enhancements to several features.
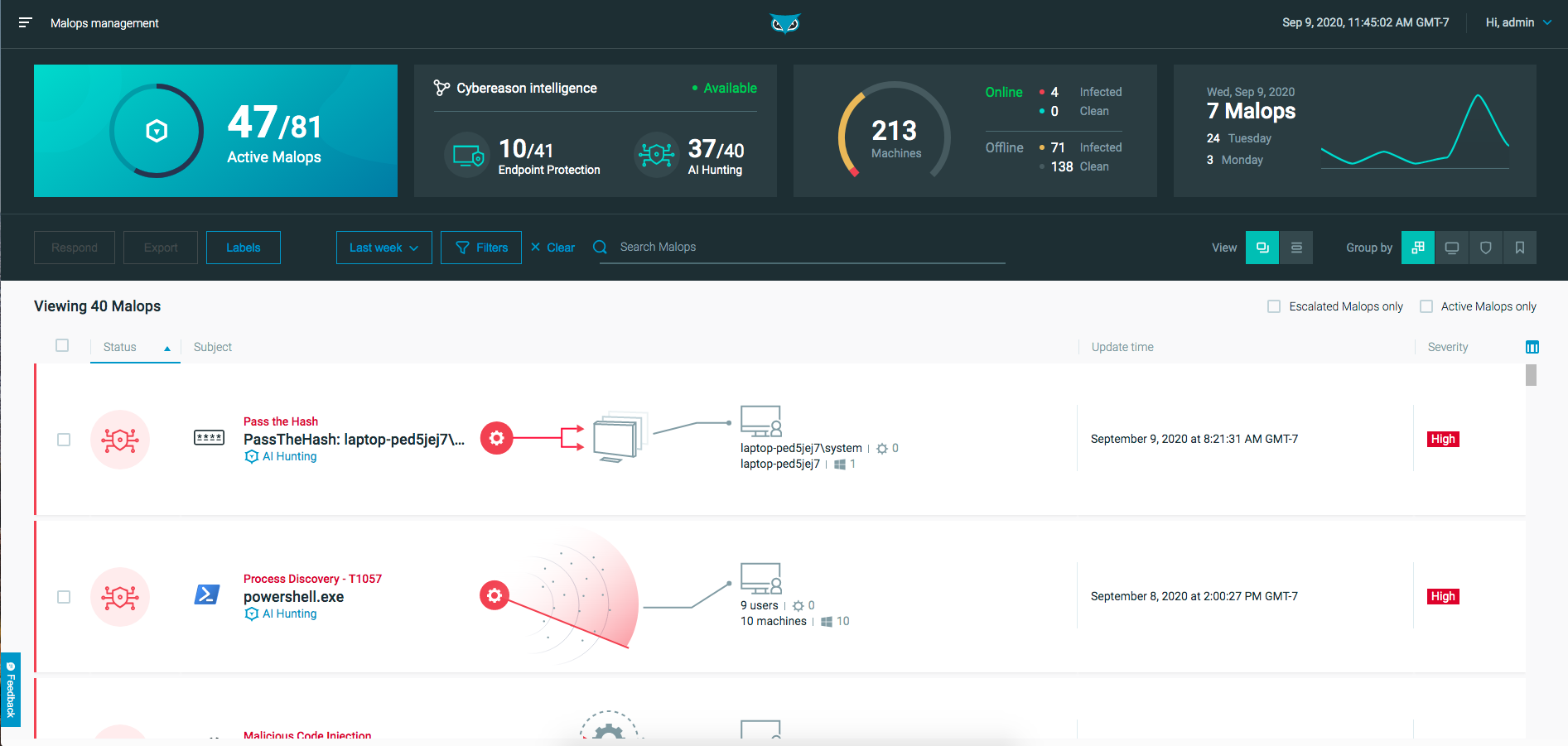
Malops management screen
With 20.1, Malops and malware alerts have been reorganized. Malware alerts are now classified as Malops, and Malops include two types: AI Hunting Malops and Endpoint Protection Malops.
AI Hunting Malops represent Malops triggered by Cybereason’s automatic hunting engine and threat intelligence services. These Malops were previously displayed in the Malop inbox.
Endpoint Protection Malops are Malops that include malware alerts and other incidents detected by Cybereason’s NGAV features. These were previously displayed in the Malware Alerts screen as malware alerts.
To view this new Malop organization, we’ve developed the Malops management screen. The Malops management screen provides analysts with a single pane from which to view, analyze, triage, and respond to threats in the environment.
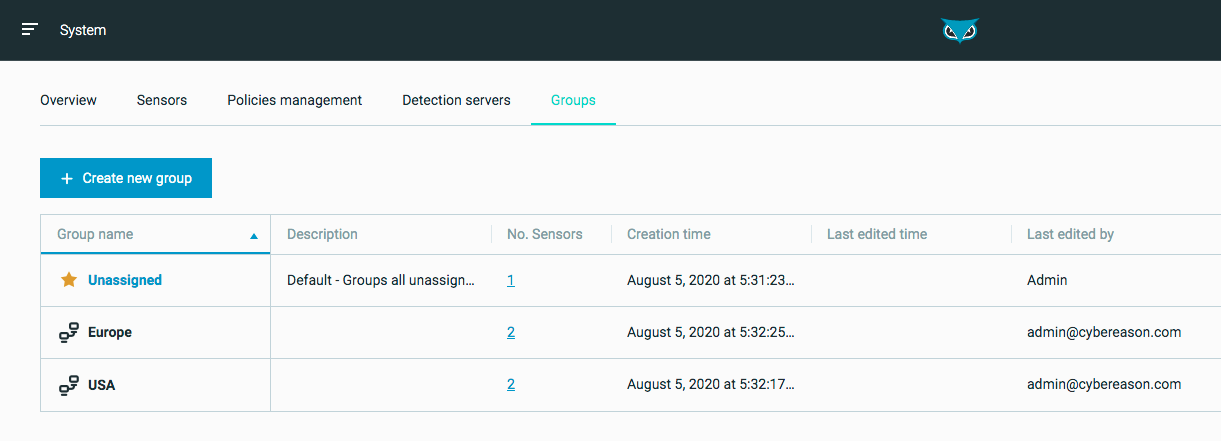
Sensor groups
To better manage sensors, system administrators can create sensor groups, and then use the new Sensor admin L1 role to grant access to each group. This feature allows system administrators to delegate sensor management and troubleshooting tasks to different users or IT teams, while limiting the access each team has to other sensors.
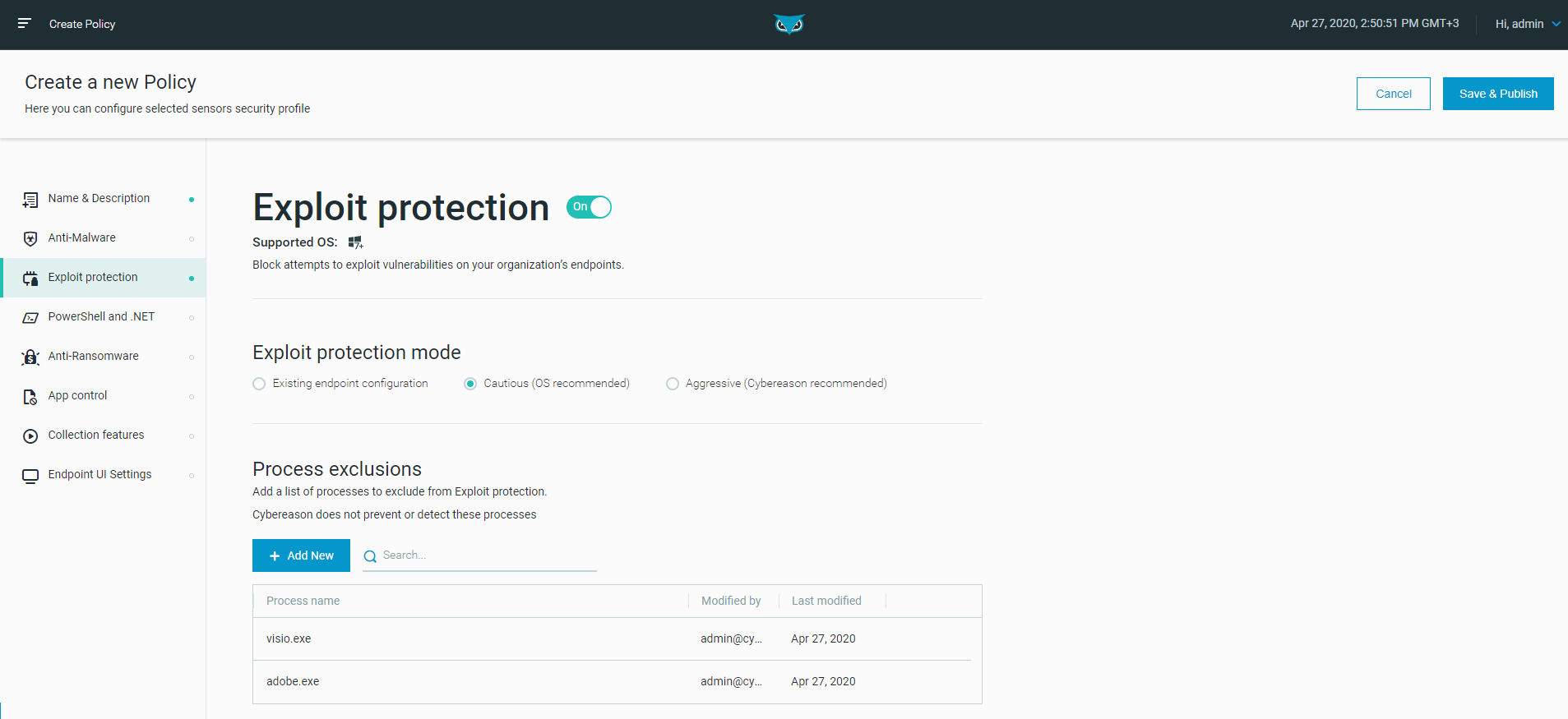
Exploit protection
Security teams and IT professionals can use the Exploit protection feature to block exploit attempts on the organization’s endpoints. Exploit protection is a Cybereason prevention feature that includes various security mitigation techniques, and is configured as part of the sensor policy. Learn more
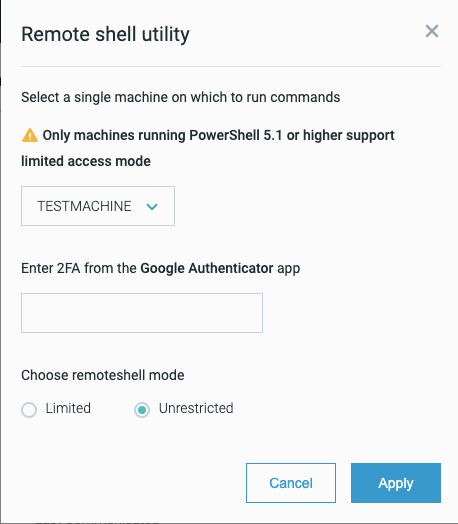
Remote shell with unrestricted mode
You can now run the Remote Shell utility in Unrestricted mode. This new mode enables you to run any PowerShell command:
In addition, the Remote Shell utility no longer requires you to have a minimum PowerShell version of 5.1 installed on the machine.
Note that when you assign a user the Responder role to enable them to use the Remote Shell utility, the user must use two-factor authentication to log into the Cybereason platform and to open a Remote Shell session.
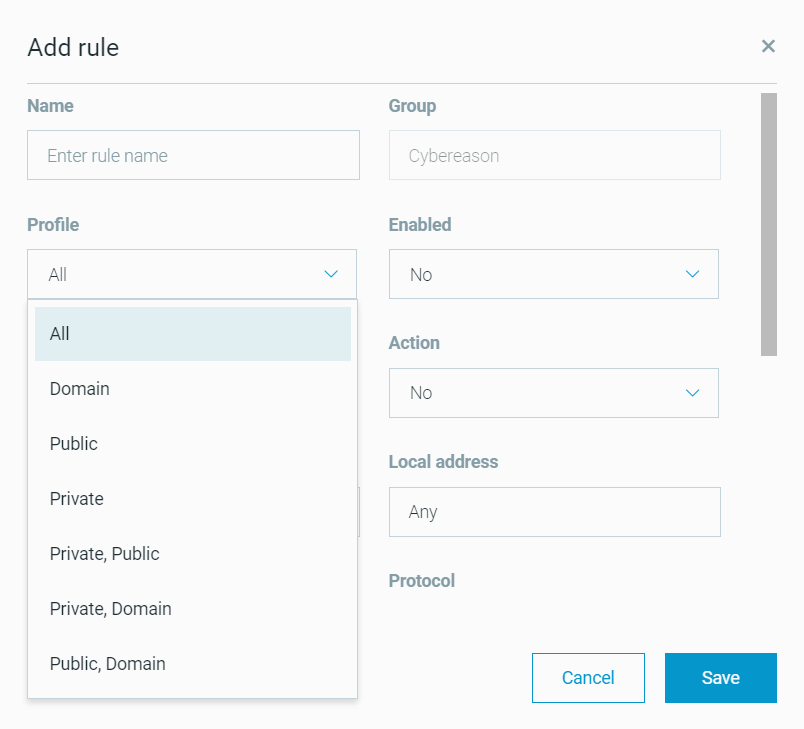
Endpoint controls - custom firewall rules enhancements
As part of the Endpoint controls feature, you can now add and edit custom firewall rules using the UI. Learn more
In addition, you can now add custom firewall rules that include Japanese text in the custom firewall rules CSV file. Learn more
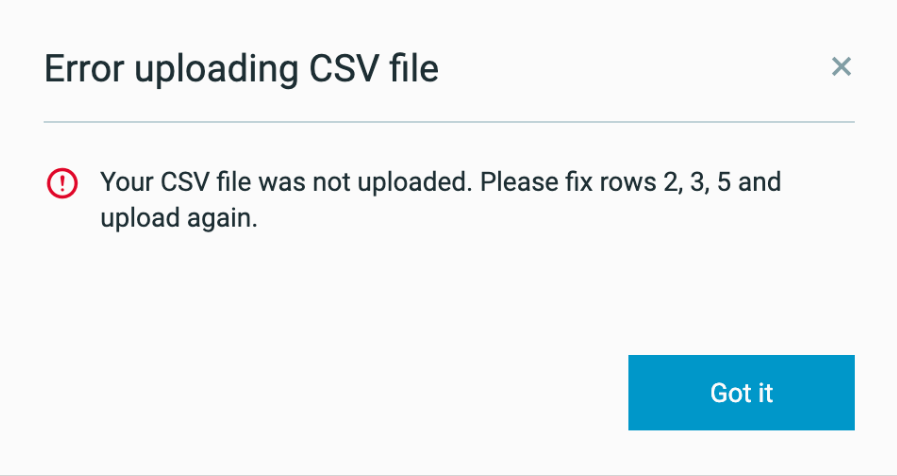
Endpoint controls - custom firewall rules protection improvements
We have introduced checks to ensure that custom firewall rules are applied and configured correctly.
When a user imports a custom firewall CSV file, the Cybereason platform now displays the Error uploading CSV file dialog box when the number of columns for a custom firewall rule does not match the number of columns in the header row.
In addition, the Cybereason platform periodically checks for misconfigured rules — for example, in cases where the Windows API applies default values or otherwise modifies the rule. Learn more
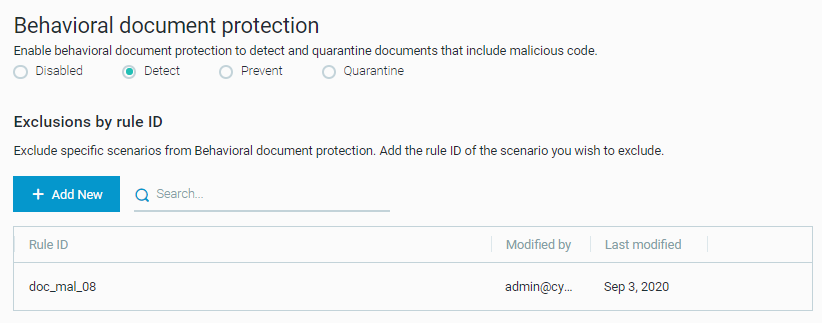
Behavioral documentation protection improvements
We have added the option to set the mode for Behavioral document protection specifically. Previously, the Signatures mode determined the way Behavioral document protection responded to threats. Learn more
In addition, you can now use Behavioral document protection in specific scenarios using rule IDs. Learn more
CVE exploit detection
We have added additional detection rules that enable you to detect the use of exploits documented in CVE reports. This includes adding a suspicion and evidence indicating a possible attempt to exploit a CVE.
In addition, we have introduced an Attempted exploitation Malop in Research mode for such attempts.
For this Malop, the Malop details report which CVE exploit the attempt tried to use.
Note
These detection rules support detection of exploits for CVE reports for which the proper operating system update is installed.
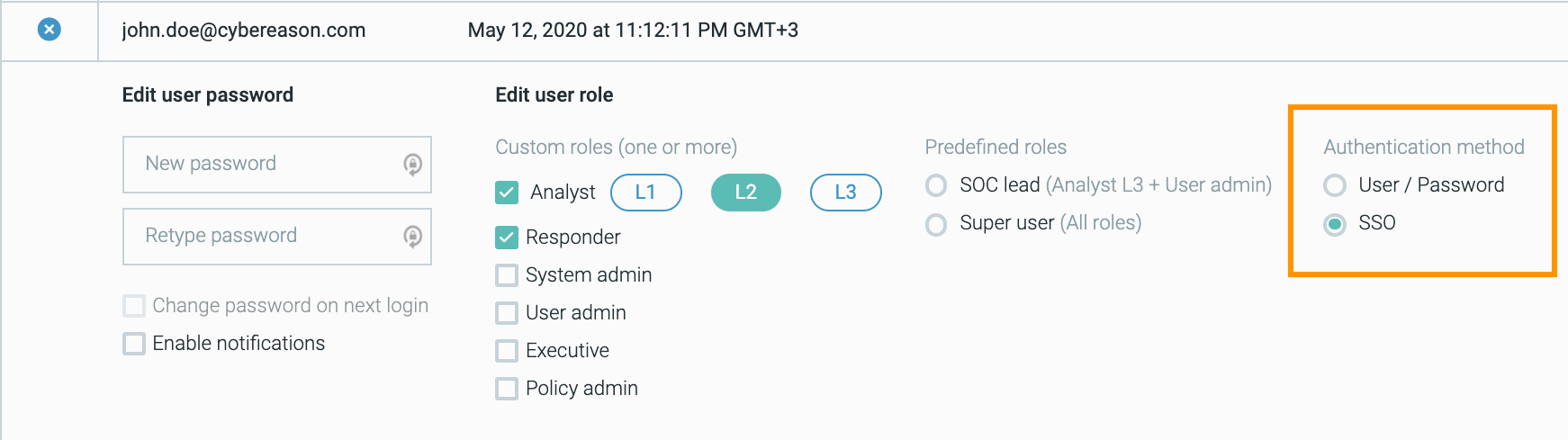
Use SSO to manage Cybereason users
Cybereason supports single sign-on (SSO) authentication for all users. Single sign-on authentication gives administrators better control over password management by allowing them to integrate their company’s current authentication services with the Cybereason UI. In addition, users can conveniently pivot between company applications and the Cybereason UI without having to remember multiple passwords.
The Single Sign On feature is in the beta stage. Contact your Customer Success representative to enable this feature.