23.1 Version Highlights
Cybereason version 23.1 LTS introduces new features, including Predictive Ranomware Protection as generally available, Behavioral Document Protection AI, and the EPP Dashboard.
In this topic:
Predictive Ransomware Protection GA
Predictive Ransomware Protection is now generally available. This new type of ransomware protection uses a multi-layered detection mechanism to identify typical ransomware behavior and prevent unknown strains of ransomware.
Predictive Ransomware use a number of different components to detect and prevent common ransomware behaviors:
Analysis of files and file activity for possible file encryption
Detection of shadow copy deletion
Detection of modifications of the Master Boot Record
In addition, the Predictive Ransomware Protection section now displays by default in a sensor policy.
For more details, see Predictive Ransomware Protection.
Behavioral Document Protection AI GA
If you use Behavioral Document Protection, sensors on version 23.1 use Behavioral Document Protection AI. Behavioral Document Protection AI utilizes a machine learning algorithm to analyze documents to identify if they contain malicious macros.
The machine learning algorithm is based on a deep neural network to provide data driven and automated selection of rules to provide enhanced protection from malicious macros contained within documents.
For more details, see Behavioral Document Protection.
EPP Dashboard
For environments with the new Data Platform infrastructure, to provide you a more useful overview of detected activity in your environment, you can use the EPP Overview dashboard screen, with a variety of different charts and graphs related to detected activity.
The Dashboard includes graphs and tables on different key data points in your environment, including:
MalOp related graphs, including Active MalOps, MalOp resolution, and so forth
MalOps by MITRE tactic
Top IOCs in your environment
To learn more about the EPP Overview dashboard, see EPP Overview Dashboard.
Anti-Malware Artificial Intelligence mode for .NET executable files
The Anti-Malware > Artificial Intelligence mode now includes enhanced coverage of .NET executable files, enabling you to more easily find new or unknown types of .NET file misuse.
For more details, see Artificial Intelligence Analysis.
Variant file prevention (beta)
Note
This feature is not generally available and in beta status. Contact your Customer Success Manager to gain access to this feature.
Beginning in this version, the Cybereason platform introduces Variant File Prevention (VFP), a pre-execution prevention engine which uses advanced fuzzy hashing techniques to quickly identify indicative similarities and patterns of known malware families.
Traditional execution prevention solutions, which rely on cryptographic hashes such as MD5, SHA-1, or SHA-256 alone, are easy to bypass. Attackers are aware that any change to the malicious file will completely change its file hash value.
To address this change, VFP compares each file with fuzzy fingerprints that are resistant to changes. Each fingerprint covers many variants of a high-value threat. If a file is found to match the fingerprint, VFP detects it as a MalOp.
For more details, see Variant File Prevention.
MalOps management improvements
To improve the experience and efficiency of using the Malops management screen, we have updated a number of different features:
Sort columns in the MalOp grid |
You can sort the displayed results in the MalOp grid by a number of different columns, such as the MalOp name, Investigation status, and so forth. |
Show or hide overview widgets |
If you do not need to use or view the overview widgets at the top of the screen, and also display additional rows of the MalOps grid, you can show or hide the widgets: |
MalOp state matches the Investigation status |
We have improved the server’s internal logic to make sure that the MalOp state more intuitively matches the Investigation status. |
Open a MalOp in a new browser tab |
You have the option to open a specific MalOp in a new browser tab to preserve the results you have currently displayed in the Malops management screen tab. |
Add the MITRE tactics and IOCs columns |
To add further additional contextual information for each MalOp, you can add the MITRE Tactics and IOCs columns in the MalOps grid. |
New filters |
We have added a number of different filters to help you find other ways to filter MalOps, including the MITRE Tactics, IOCs, and Protection type filters. |
MalOp management screen URL reflects the currently filter context |
When you add a filter in the MalOp grid, the URL displayed in your browser changes to show the filter currently in use. |
For more details, see View MalOps with the New Data Platform.
Decommission sensors from your environment
To help you remove sensors that you no longer manage or cannot reach to uninstall a sensor, we have added the ability to Decommission a sensor. Decommissioning a sensor removes the sensor’s connection with the Cybereason platform and adds the sensor to a schedule to uninstall the sensor and delete it from your Cybereason environment.
The Decommission action also works with the existing Stale and Archived sensor flows, as you configure the ability and time interval from when to automatically decommission archived sensors.
For details on how to decommission a sensor, see Remove Sensors from Monitoring.
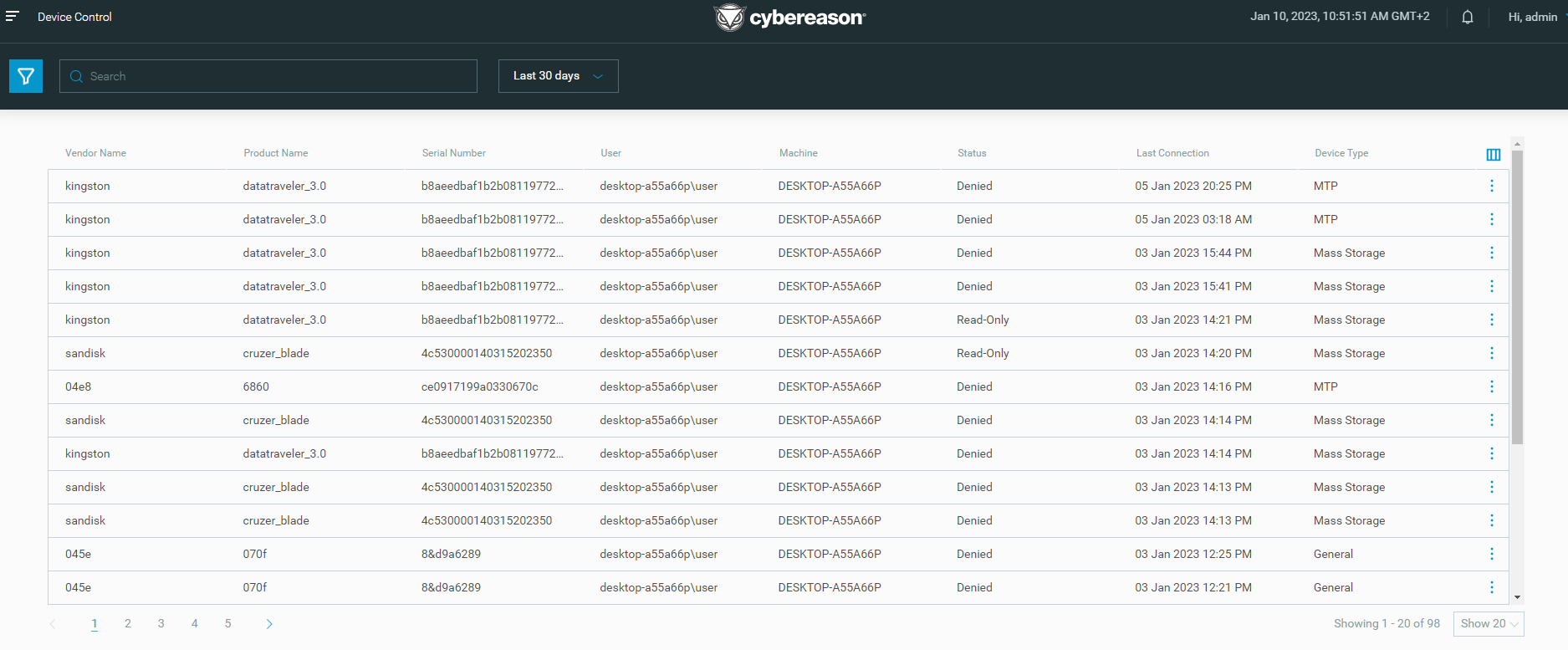
Device Controls screen
Note
This feature is not generally available and in beta status. Contact your Customer Success Manager to gain access to this feature.
Beginning in this version, you can use the Device Controls screen to view Device control events on machines connected to the Cybereason platform and easily monitor the usage of USB devices across your environment.
For more details, see View Device Control Events and Monitor USB Usage.
Assign custom reputations to specific sensor groups
If your environment has sensor grouping enabled, you now have the ability to specify sensor groups for a reputation.
The reputation is then applied when an item is detected by a sensor in the specified group, which being ignored by senors in other groups.
For details on sensor groups and reputations, see Manage Reputations.
Allow non-analysts to view MalOp information
To allow users to view MalOp information and details without the ability to edit MalOp details (e.g. Comments, Labels) or change MalOp investigation statuses, we have added the L1 Analyst Viewer or Local L1 Analyst Viewer roles.
Users with these roles can view MalOp and MalOp details and the Investigation screen, but cannot edit items in these screens.
NGAV usability improvements
This version also introduces a number of enhancements to improve the performance and usefulness of Cybereason NGAV.
For MalOps generated by Fileless Protection, the MalOps include descriptions for rule-based (pattern) Fileless detection events. These description of the malicious behavior associated with the pattern help analysts better understand the context of the event. You can view the descriptions in the Malop details and Investigation screens.
Note
These descriptions are not available by default. Open a Technical Support case to enable this feature.
In addition, Fileless protection adds significant enhancements to provide better stability over time and accommodate larger environments with numerous exclusions.
Lastly, the Anti-Malware section of your sensor policy adds a Disable USN Journals option in the Signatures section to stop Anti-Malware protection from scanning the Windows USB Journals on a machine.
Assign machine isolation exception rules for different sensor groups
You can now assign machine isolation exception rules to specific sensor groups. This helps limit access to various endpoint machines to your analysts and admins depending on their group permissions.
For details on machine isolation exception rules, see Machine Isolation Exception Rule.
Assign sensors to groups based on OS and FQDN attributes
When creating rules for automatic assignment of sensors to sensor groups, in addition to existing fields, you can now assign sensors based on the operating system type and sensor FQDN.
Note
This feature is not available by default. Open a Technical Support case to enable this feature.
For details on creating rules for automatic assignment of sensors to sensor groups, see Build group assignment logic.
Obfuscation of sensor policy exclusions in sensor logs
On sensors running supported versions of macOS and Linux, sensor policy exclusions are obfuscate to prevent this information from being misused by attackers.
Collect device model and serial numbers from macOS machines
On macOS machines, sensors not collect the Device model and Serial number of the machine to help with investigation and machine identification
New OS support
We have added support for the following new operating systems:
A Early access version for Linux ARM, including core security functionality. Automatic installation and visibility of these sensors in the Sensors screen is not yet supported.
AlmaLinux 8.6, 8.8, 8.10, 9.2, and 9.4
To get access to the Linux ARM sensor package, open a Technical Support case.